OpenAI Introduces Codex Security to Detect and Fix Software Vulnerabilities
Artificial intelligence is continuing to reshape the way organizations build and secure…
Safeguard your sensitive information with proactive monitoring, real-time alerts, and robust data protection strategies.
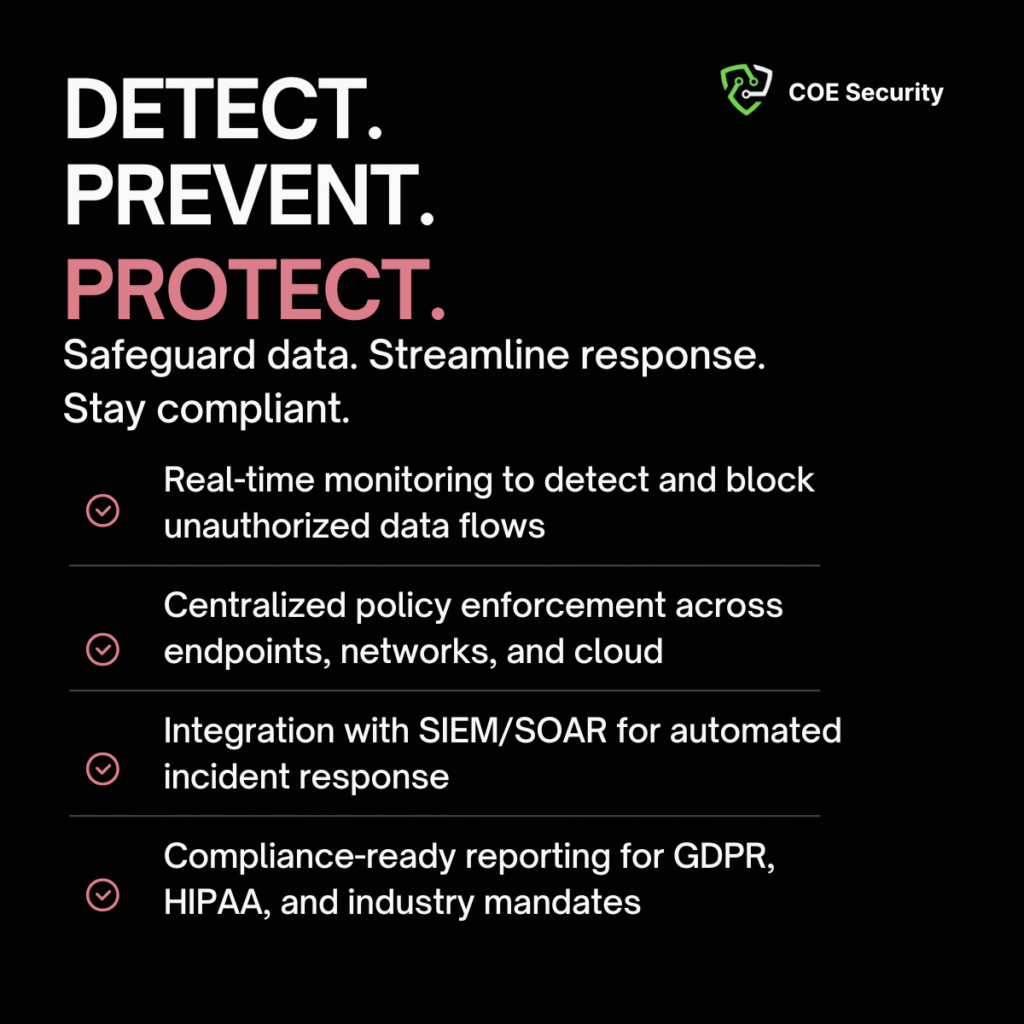
At COE Security, our Data Leak Prevention (DLP) Security Operations are designed to safeguard your sensitive data from unauthorized access, misuse, and exfiltration. With increasing volumes of confidential data being shared across endpoints, cloud platforms, and collaboration tools, having a proactive DLP strategy is essential to prevent accidental or malicious data leaks.
Our DLP operations provide continuous visibility and control over how data is accessed, shared, and stored. We deploy advanced monitoring and enforcement mechanisms across networks, endpoints, and cloud services to detect and block risky activities in real time. Whether it’s intellectual property, customer information, or regulated data, our solutions help you stay compliant and secure.
By integrating DLP with your broader security operations, COE Security empowers your organization to reduce data exposure risks and maintain trust with clients, partners, and regulators.
Define Data Protection Objectives and Scope: Identify sensitive data types, business-critical assets, and applicable regulatory requirements to define clear DLP goals and operational boundaries.
Classify Sensitive and Regulated Data: Use automated tools to discover, tag, and classify sensitive data across endpoints, networks, cloud, and storage systems to enforce tailored protection policies.
Deploy DLP Policies and Controls: Implement DLP rules and security controls to monitor, detect, and prevent unauthorized access, transfer, or misuse of classified data across all channels.
Integrate DLP with SIEM and SOC Workflows: Connect DLP tools with SIEM platforms and SOC operations to ensure real-time alerting, contextual analysis, and coordinated incident response.
Monitor Data Movement and Usage Patterns: Continuously track data flows, user behavior, and access patterns to detect anomalies that may indicate insider threats or data exfiltration attempts.
Implement Endpoint and Network DLP Agents: Deploy endpoint and network-level DLP agents to enforce policies, monitor activity, and block or alert on policy violations in real time.
Develop Incident Response Playbooks: Create playbooks for common data leak scenarios, including insider misuse, shadow IT, and cloud sharing risks, to guide fast and consistent responses.
Train Users and Raise Awareness: Conduct regular awareness sessions and phishing simulations to educate employees about data protection policies and safe data handling practices.
Audit and Improve DLP Effectiveness: Regularly review DLP alerts, false positives, policy coverage, and response actions to refine controls and improve detection accuracy.
Generate Compliance and Risk Reports: Provide detailed reports to management and auditors that demonstrate data protection measures, incidents handled, and regulatory alignment.
Comprehensive Data Visibility: COE Security delivers end-to-end monitoring of sensitive data across endpoints, networks, cloud, and user interactions.
Tailored DLP Policy Frameworks: We design and deploy custom policies based on your data types, industry needs, and regulatory obligations.
Real-Time Threat Detection: Our integrated DLP-SIEM workflows detect and respond to leaks or misuse instantly, minimizing data exposure.
Expert Incident Response Playbooks: We implement playbooks that guide efficient and consistent responses to different data breach scenarios.
Advanced Insider Threat Detection: COE Security identifies behavioral anomalies and suspicious access patterns to mitigate insider risks.
User Awareness Integration: We support your workforce with ongoing training to reduce accidental data leaks and reinforce secure practices.
Seamless Integration with Existing Tools: Our DLP solutions integrate with your current security stack, including EDR, SIEM, IAM, and cloud platforms.
Continuous DLP Optimization: We continuously refine rules, reduce false positives, and enhance detection accuracy through active SOC tuning.
Compliance-Centric Reporting: Our reporting templates map directly to GDPR, HIPAA, ISO 27001, and other regulatory frameworks.
Proven Experience in DLP Operations: With a strong track record in data protection, COE Security ensures your critical data remains secure and compliant.

Application Security Posture Management (ASPM) is crucial for preventing data leaks by continuously assessing and strengthening the security posture of your applications. Our team monitors and evaluates your software’s security configurations, identifying potential vulnerabilities that could lead to data breaches. By implementing automated tools and periodic vulnerability assessments, we ensure that your applications are consistently protected against evolving threats. ASPM helps you maintain a proactive security strategy, making it harder for attackers to exploit weaknesses in your applications, thus minimizing the risk of unauthorized data access and leakage. Regular updates and security patches are crucial in safeguarding sensitive data.

Effective Application Security Consulting focuses on implementing robust security measures throughout the entire software development lifecycle to protect against potential data leaks. We work closely with your development teams to ensure that security is integrated from the earliest stages of design through to deployment. Our consultants conduct thorough code reviews, penetration testing, and threat modeling, helping you identify and address security vulnerabilities that could lead to data leaks. With guidance on best practices, including secure coding techniques and vulnerability remediation, we ensure that your applications are fortified against the risks that could compromise sensitive information and lead to compliance issues.
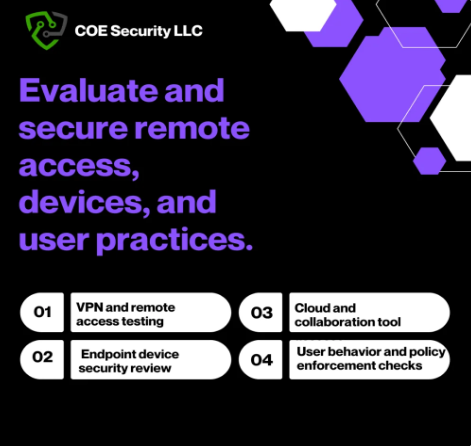
As remote work becomes increasingly common, securing data across distributed environments is more important than ever. Our Remote Work Security Assessment focuses on securing access to critical data and applications for remote employees, minimizing the risk of data leaks. We evaluate your organization’s remote work policies, virtual private networks (VPNs), endpoint security, and user access controls to identify vulnerabilities. With comprehensive assessments and tailored solutions, we ensure that remote work setups are secure, preventing unauthorized access and data exfiltration. Our goal is to provide secure communication channels and data access protocols that protect sensitive information in a remote work environment, ultimately safeguarding against potential data leaks.

Cloud environments present unique challenges for data security and leak prevention, especially as organizations scale their cloud infrastructures. Our Cloud Security Consulting services ensure that your cloud platforms, services, and applications are configured securely to prevent unauthorized data access and leakage. We assess cloud storage systems, identity and access management, encryption practices, and data sharing policies to identify potential gaps in security. Our expert team works with you to implement secure cloud security frameworks, applying encryption at rest and in transit, multi-factor authentication, and other vital measures to protect sensitive data in cloud environments. With our support, you can confidently scale your cloud infrastructure while ensuring your data remains protected from leaks.

Building Cyber Resilience is essential in protecting your organization against data leaks that could occur due to cyber incidents. We help you develop and implement a comprehensive cyber resilience strategy that focuses on both preventing data breaches and ensuring rapid recovery in the event of a leak. Our team identifies critical assets and implements advanced threat detection systems, including anomaly detection and incident response plans, to quickly identify and mitigate any potential data leak incidents. By establishing strong data protection protocols, regular backups, and secure recovery processes, we ensure that your organization can maintain its operations while minimizing the damage of any security breaches.
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Certified cybersecurity professionals you can trust.
Testing aligned with OWASP, SANS, and NIST.
Clear reports with practical remediation steps.















Artificial intelligence is continuing to reshape the way organizations build and secure…
As artificial intelligence becomes more deeply integrated into business operations, new types…
The modern cyber threat landscape is evolving beyond traditional attack vectors. Increasingly,…