Center of Excellence Security - Cyber Resilience
Build a Resilient Cyber Future!
Ensure business continuity and rapid recovery with our comprehensive cyber resilience solutions.
Cyber Resilience at COE Security

At COE Security, we understand that in today’s rapidly evolving digital landscape, it’s not just about preventing cyberattacks but also about ensuring your organization can quickly recover when an attack occurs. Our Cyber Resilience solutions are designed to help your business maintain operations in the face of disruption, ensuring business continuity, and minimizing the impact of cyber incidents.
Our approach to cyber resilience combines proactive risk management with robust recovery strategies. We work with your team to implement advanced security measures, develop incident response plans, and establish backup and recovery processes that ensure minimal downtime. By building resilience into your cybersecurity framework, we help you not only defend against attacks but also quickly return to normal operations with as little disruption as possible.
With COE Security’s Cyber Resilience solutions, your organization can confidently navigate the complex threat landscape and be prepared for any cyber event, from ransomware attacks to data breaches, ensuring that your critical business functions remain intact.
Our Approach
Assess Organizational Risks and Threat Landscape: Identify critical assets, operations, and dependencies, evaluating how cyber threats may impact business continuity.
Define Cyber Resilience Strategy: Establish clear objectives for maintaining business operations during and after a cyber incident, aligned with overall business goals.
Develop Incident Response and Recovery Plans: Create a comprehensive plan to detect, respond to, and recover from cyberattacks, ensuring minimal disruption to business functions.
Implement Redundancy and Failover Systems: Design backup systems and failover mechanisms to ensure continuous availability of critical services, even during attacks.
Strengthen Security Posture with Layered Defenses: Deploy multiple layers of security controls firewalls, encryption, endpoint protection, and intrusion detection systems across the infrastructure.
Integrate Business Continuity and Disaster Recovery: Align cybersecurity efforts with business continuity and disaster recovery plans to ensure swift recovery from disruptions.
Continuously Monitor and Detect Threats: Set up advanced monitoring tools to detect anomalies and potential threats in real-time, minimizing response time during incidents.
Regularly Test and Simulate Cyber Resilience Scenarios: Conduct tabletop exercises, penetration tests, and breach simulations to evaluate response readiness and resilience.
Ensure Secure Data Backups and Recovery Procedures: Regularly back up critical data and implement secure recovery procedures to prevent data loss and facilitate rapid recovery.
Review and Improve Cyber Resilience Measures: Continuously evaluate the effectiveness of your resilience strategy and update plans based on lessons learned and emerging threats.
Business Continuity Planning
Incident Response & Recovery
Risk Assessment & Mitigation
Regular Testing & Simulation
Cyber Resilience Process
Assess
Plan
Implement
Test & Simulate
Optimize
Why Choose COE Security’s Security's Cyber Resilience?
Comprehensive Risk and Threat Analysis: We identify key vulnerabilities and potential threats, building a resilience strategy tailored to your organization.
Proactive Business Continuity Planning: Our approach ensures that your organization remains operational, even during a major cybersecurity incident.
Multi-Layered Defense Strategy: We implement robust security measures to prevent and mitigate attacks across all levels of your infrastructure.
Seamless Incident Response Integration: Our resilience plans are closely aligned with your incident response protocols for fast, effective recovery.
Business-Aligned Resilience Framework: We develop strategies that integrate cyber resilience with your business objectives, ensuring both security and operational continuity.
Ongoing Monitoring and Detection: We implement real-time monitoring systems to detect threats as they emerge, minimizing downtime and damage.
Realistic Cyberattack Simulations: We conduct simulations to assess your preparedness and improve response tactics under pressure.
Data Integrity and Availability Assurance: Our strategies ensure your critical data is secure, backed up, and recoverable, protecting against data loss.
Scalable Resilience Solutions: We provide solutions that grow with your organization, adapting to new risks and challenges as they arise.
Trusted Expertise in Cyber Resilience: COE Security brings proven expertise in helping organizations build, test, and maintain effective cyber resilience strategies.
Five areas of Cyber Resilience

Compliance as a Service
Navigating regulatory requirements and ensuring compliance with industry standards can be complex. Our Compliance as a Service training simplifies this process by helping your team understand the critical compliance frameworks that impact your organization. From GDPR and HIPAA to industry-specific standards like PCI DSS, our program ensures your teams are well-versed in the necessary compliance obligations. Through expert guidance and real-world case studies, we show your organization how to implement and maintain compliance measures that not only help avoid penalties but also bolster your overall cyber resilience by mitigating regulatory risks.

Security Program Development
Building a strong security program is fundamental to long-term cyber resilience. Our Security Program Development training focuses on creating a comprehensive security strategy tailored to your organization’s needs. We guide your team through the process of establishing policies, defining risk management protocols, and developing a sustainable security architecture. Topics covered include governance, risk assessments, vulnerability management, and incident response. By the end of the training, your team will have the knowledge to implement and continuously improve a security program that reduces risks, aligns with compliance mandates, and strengthens your organization’s overall defense mechanisms.

SOC as a Service (SOCaaS)
At COE Security LLC, our SOC as a Service (SOCaaS) offering provides organizations with 24/7 security monitoring, threat detection, and incident response capabilities. Leveraging cutting-edge technologies and expert analysts, we monitor your IT environment for suspicious activities and vulnerabilities. Our SOCaaS includes real-time threat intelligence integration, advanced SIEM (Security Information and Event Management) tools, and detailed incident reporting. With tailored alerts, proactive defense strategies, and compliance support, we ensure a comprehensive and scalable solution. Let COE Security be your partner in enhancing cybersecurity resilience, mitigating risks, and safeguarding your business against evolving threats.
Supply Chain Security Review
Supply chain vulnerabilities can be an easy target for cybercriminals looking to infiltrate your systems. Our Supply Chain Security Review training focuses on identifying and mitigating risks within your supply chain. This training covers best practices for securing vendor relationships, assessing third-party security postures, and understanding how cyber risks within your supply chain can affect your organization’s overall security. We guide your team on how to implement a continuous review process to monitor and manage supply chain risks, ensuring that external partners meet the necessary security standards. By the end of this training, your organization will be better prepared to protect sensitive data from vulnerabilities across your entire supply chain.

Enterprise Security Strategy Consulting
A comprehensive security strategy is essential for safeguarding your organization’s assets and maintaining operational resilience. Our Enterprise Security Strategy Consulting training helps senior leaders and security teams create and implement a robust security strategy that aligns with business objectives. We focus on understanding the organization’s risk landscape, aligning security efforts with business priorities, and developing a long-term roadmap for enhancing cyber resilience. Participants will gain insights into threat intelligence, proactive defense measures, and disaster recovery planning, enabling them to create a forward-thinking security strategy that is adaptable to changing cyber threats and business needs.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
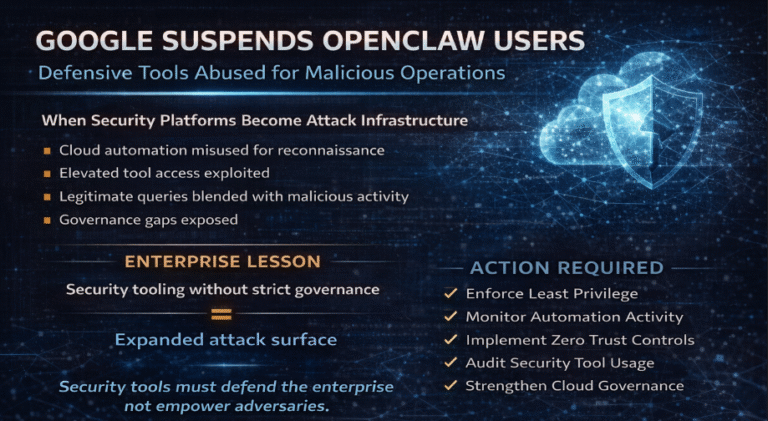
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…