Protecting Company Data in 2026

In 2026, protecting company data is no longer just an IT responsibility-it is a core business survival issue. With cloud-first operations, remote workforces, AI-powered tools, and complex vendor ecosystems, a single weak link can expose an organization’s most valuable asset: its data. Founders and executive teams must now treat data protection as a strategic governance […]
Critical WatchGuard VPN Client Flaw

A critical security vulnerability has been discovered in the WatchGuard VPN Client for Windows that allows attackers to execute commands with SYSTEM-level privileges. This represents the highest level of access on a Windows system and can result in full device and network compromise. This flaw highlights a growing reality in modern cybersecurity: endpoint software and […]
Ransomware Attacks Surge in 2026

The ransomware threat landscape has entered a new phase in 2026-one defined by scale, automation, and sector-specific targeting. Recent industry reporting and threat intelligence confirm a sharp rise in ransomware activity, with healthcare and manufacturing emerging as two of the most heavily targeted sectors. Attack volumes in 2025 closed at record highs, and early 2026 […]
Vibe Crime Is Here

Cybercrime has entered a new operational era. According to Trend Micro, cybercriminals are rapidly adopting agentic AI -autonomous AI systems capable of planning, executing, and optimizing attacks with minimal human involvement. This emerging threat model is being described as “vibe crime.” Unlike traditional cyberattacks that rely on manual coordination, vibe crime represents a shift to […]
AI Fuels Cyber Scams

The rapid evolution of artificial intelligence has revolutionized the digital landscape, offering powerful tools that transform industries and everyday life. However, this technological progress also provides cyber criminals with advanced means to launch sophisticated scams. Generative AI tools such as ChatGPT, deepfake generators, and voice cloning software are now being weaponized to create highly convincing […]
BugTrace AI
Penetration testing is evolving. As applications grow more complex, traditional approaches built around broad scanning and manual reconnaissance are increasingly inefficient. Modern environments span APIs, cloud-native architectures, client-side logic, and third-party integrations. While tooling has advanced, much of a pentester’s time is still spent identifying where to look rather than validating what actually matters. This […]
AiTM Phishing Attacks

Enterprise email remains the most abused and effective attack surface in cybersecurity. But the nature of phishing has fundamentally changed. Microsoft has issued warnings about a new wave of highly sophisticated Adversary-in-the-Middle (AiTM) phishing attacks that are actively targeting enterprise email systems, bypassing multi-factor authentication (MFA) and enabling large-scale account takeover. This is not traditional […]
Critical Enterprise Risk

In today’s interconnected enterprise environments, firewalls represent the first and last line of defense. They sit at the network perimeter, enforce access controls, inspect traffic, and protect critical internal systems. Yet, in the last 24 hours, a serious and unsettling security development has emerged: Fortinet FortiGate firewalls are being actively compromised through a FortiCloud SSO […]
Ancillary Systems Are High-Value Targets
On December 15, 2025, SoundCloud confirmed unauthorized access to user data affecting approximately 20% of its global user base. The attackers exfiltrated email addresses and public profile information. Importantly, no passwords, authentication secrets, or financial data were compromised. From a narrow technical perspective, this distinction matters. It prevented immediate account takeover, direct financial fraud, and […]
chained exploitation technique
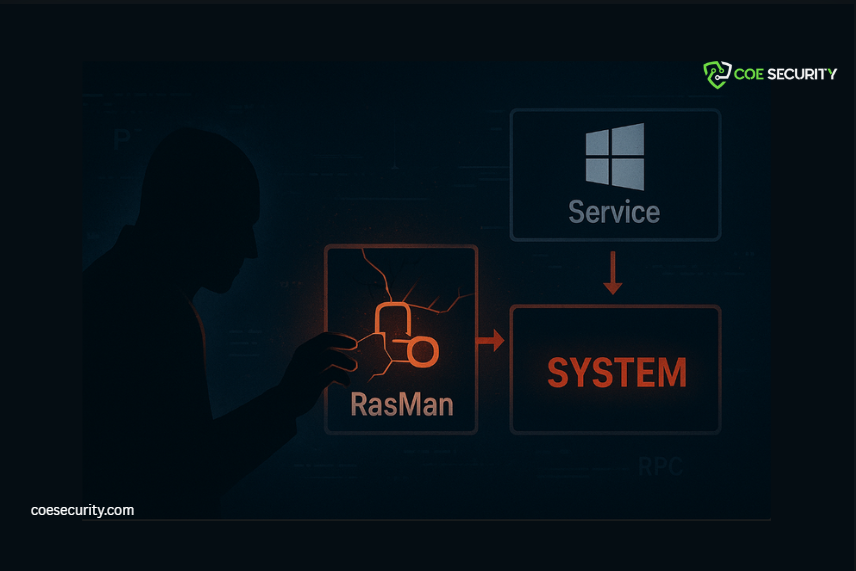
A critical weakness has been identified in Windows Remote Access Connection Manager (RasMan) that enables local attackers to achieve SYSTEM-level code execution. What makes this issue especially dangerous is not a single vulnerability-but a chained exploitation technique that breaks long-standing Windows security assumptions. Executive Summary Impact: Full local privilege escalation to NT AUTHORITY\SYSTEM Attack Type: […]
