Golden SAML: Identity Threat
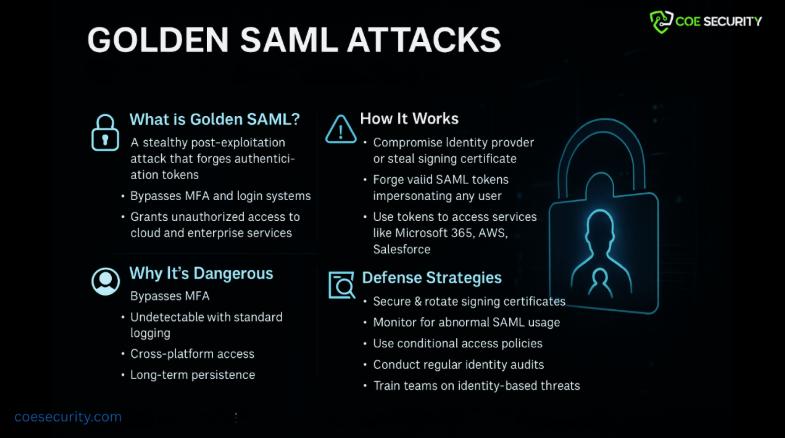
In today’s rapidly evolving digital environment, the security of identity systems has become paramount. Federated authentication, which relies on trust relationships between identity providers (IdPs) and service providers (SPs), has made it easier for users to access multiple services using a single set of credentials. However, this convenience comes at a cost. A relatively unknown […]
Cyber War on Food Supply

On June 5, 2025, the digital heartbeat of North America’s food distribution suffered a sudden cardiac arrest. United Natural Foods Inc. (UNFI), the largest wholesale grocery supplier on the continent, was brought to its knees by a cyberattack. What followed was not just a systems outage but a tangible ripple that emptied grocery shelves and […]
Scania Hack: Third-Party Risk

A recent cyberattack on Scania, the well-known Swedish truck maker and financial services provider, has underscored a growing threat: external partner vulnerabilities are opening doors to serious data breaches. In late May, attackers used credentials stolen via malware from an external IT vendor to infiltrate Scania’s insurance portal. The attackers stole approximately 34,000 insurance claim […]
Deepfake Threat: BlueNorof

Introduction In the ever-evolving cybersecurity landscape, threat actors continue to innovate, leveraging cutting-edge technologies to bypass defenses. A chilling example is the recent attack orchestrated by the BlueNoroff group, a subset of the Lazarus Group, which targeted cryptocurrency firms using deepfake technology during Zoom calls. This incident underscores the critical need for robust cybersecurity measures […]
Nobitex Breach: $90M Signal

In the pre-dawn hours of a seemingly ordinary Wednesday, the digital vaults of Nobitex Iran’s largest cryptocurrency exchange fell silent. But this wasn’t a case of routine maintenance. This was cyberwarfare, cloaked in political symbolism and fueled by decades of international tension. The hacker group known as Gonjeshke Darande (Predatory Sparrow) emerged once again from the depths […]
GodFather Malware: Mobile Risk

In the ever-evolving world of mobile cyber threats, a recent discovery has shaken the financial and cybersecurity communities alike. A new strain of the notorious GodFather banking malware has emerged with a level of sophistication that transcends traditional attack methods. This time, the malware doesn’t just mimic banking screens – it creates an entire virtual environment on the victim’s […]
Ransomware Hits Dairy Tech

In the quiet corners of America’s heartland, where early morning sun glints off silver silos and the rhythm of dairy production hums along, a silent threat has made its way into the barn: ransomware. Recently, Dairy Farmers of America (DFA), the largest dairy cooperative in the United States, disclosed that several of its manufacturing facilities […]
Water Curse: Supply Chain Hit

In a landscape increasingly dependent on open-source software, a new and insidious threat has emerged: a campaign orchestrated by a group identified as Water Curse, which has weaponized trust itself. Discovered in May 2025, yet active since early 2023, Water Curse has strategically infiltrated GitHub, leveraging at least 76 fraudulent accounts to distribute trojanized repositories. These […]
Ransomware & Health: 2025

The Unyielding Surge of Cyber Threats in Healthcare In 2025, the healthcare sector continues to grapple with an escalating tide of cyber threats, positioning it as a primary target for malicious actors. The inherent value of sensitive patient data, combined with the often complex and interwoven digital infrastructures, renders healthcare uniquely susceptible to cyber intrusions. […]
Hidden Malware in Open Code
The open-source community has long been a bedrock of innovation and collaboration. But beneath the surface, a darker current flows, one that cyber attackers have learned to exploit with growing sophistication. In a recent wave of disclosures, researchers uncovered malicious packages lurking in widely-used repositories like PyPI and npm, targeting developers and organizations through the […]
