Center of Excellence Security -Merger & Acquisition Security Consulting
Secure Your M&A Transactions with Confidence!
Mitigate risks, ensure compliance, and drive seamless integrations with our expert merger & acquisition security consulting services.
Merger & Acquisition Security Consulting at COE Security

At COE Security, our Merger &Acquisition (M&A) Security Consulting service helps organizations navigate the complex security challenges that arise during mergers, acquisitions, or business integrations. As businesses consolidate or acquire new entities, ensuring that security risks are properly assessed and managed is crucial to protecting intellectual property, sensitive data, and business operations. Our M&A Security Consulting service provides expert guidance in identifying potential security vulnerabilities and ensuring a smooth integration of security infrastructures.
We partner with organizations across the M&A lifecycle to assess the security posture of both parties, identify risks early, and embed security into due diligence. We also support secure, compliant integration of systems and data while minimizing business disruption. With COE Security’s M&A Security Consulting, you gain the confidence that your mergers and acquisitions are secure, compliant, and aligned with your long-term business goals.
Our Approach
Define Security Objectives and Scope: Establish the security goals for the merger or acquisition, including the scope of due diligence, integration requirements, and key security risks associated with the transaction.
Conduct Security Due Diligence: Perform an in-depth security assessment of both organizations involved in the M&A, reviewing cybersecurity policies, protocols, asset inventories, and any existing security gaps.
Identify Critical Assets and Risks: Identify and assess the critical digital assets, intellectual property, and sensitive data that need to be protected during the merger or acquisition process.
Assess Compliance and Regulatory Impact: Evaluate the legal and regulatory requirements for both companies, ensuring compliance with standards such as GDPR, HIPAA, and industry-specific regulations that might affect the deal.
Perform a Vulnerability Assessment: Conduct vulnerability assessments of both companies’ IT infrastructures, identifying potential security weaknesses that could be exploited during the transition or integration.
Evaluate IT and Cybersecurity Frameworks: Assess the current IT and cybersecurity frameworks of both entities to identify discrepancies in policies, tools, and practices that could lead to integration challenges or security risks.
Design an Integration Security Strategy: Develop a comprehensive security strategy for merging the two organizations’ networks, systems, and processes, addressing any gaps and ensuring secure data migration and system compatibility.
Implement Access Control and Data Segmentation: Establish strong access controls and data segmentation strategies to ensure that sensitive information remains protected during and after the merger or acquisition.
Prepare Incident Response and Disaster Recovery Plans: Update incident response and disaster recovery plans to account for potential security breaches or system disruptions during the M&A process, ensuring rapid recovery.
Monitor and Audit Post-M&A Security: Conduct ongoing monitoring and audits post-merger to evaluate the effectiveness of the security measures and to ensure that no new vulnerabilities have emerged due to the integration.
Due Diligence & Risk Assessment
Security Integration Planning
Compliance & Regulatory Alignment
Incident Response & Contingency Planning
Merger & Acquisition Security Consulting Process
Our established IoT penetration testing methodology delivers comprehensive testing and actionable recommendations.
Assess
Strategize
Implement
Monitor & Adapt
Review & Optimize
Why Choose COE Security’s Merger & Acquisition Security Consulting?
Comprehensive Security Assessment: We provide a thorough security assessment during M&A, identifying all potential risks and vulnerabilities that could compromise the transaction or post-acquisition integration.
Expertise in M&A Security: COE Security’s team has extensive experience in securing complex mergers and acquisitions, helping organizations successfully navigate security challenges during the transaction process.
Regulatory and Compliance Focus: Our consultants ensure that your M&A process meets all regulatory requirements and industry-specific standards, mitigating the risk of non-compliance during the deal.
Tailored Security Strategies: We develop customized security strategies to address the unique needs and complexities of your M&A, including both technical and organizational considerations.
End-to-End Security Support: From due diligence to post-acquisition integration, we offer comprehensive security consulting that supports your organization throughout the entire M&A process.
Risk Mitigation: We focus on identifying and mitigating risks early, protecting your organization from potential security breaches, data leaks, and other threats that could derail the deal.
Seamless Integration Planning: Our experts work to ensure that your IT infrastructure, cybersecurity frameworks, and business operations are seamlessly integrated with minimal security disruptions.
Incident Response Preparedness: We help you prepare for any potential security incidents during the merger, equipping your teams with effective response plans and protocols to minimize damage.
Post-M&A Monitoring and Auditing: We provide continuous post-acquisition monitoring and auditing to ensure that all security systems remain effective and no new vulnerabilities are introduced during integration.
Proven Track Record: COE Security has a successful history of securing high-value mergers and acquisitions, ensuring the protection of critical assets and maintaining business continuity throughout the process.
Five areas of Merger & Acquisition Security Consulting

Compliance as a Service
During mergers and acquisitions, ensuring that both organizations align on compliance standards is critical. Our Compliance as a Service offering helps assess and integrate the compliance posture of both the acquiring and target companies. We ensure that data protection, privacy laws, and regulatory standards are adhered to throughout the transition. Whether it’s GDPR, HIPAA, or industry-specific regulations, we review the security and compliance frameworks of both organizations, identifying any gaps that could lead to compliance violations post-merger. This service minimizes legal risks, ensuring that the acquisition complies with all relevant standards, making the transition smoother and reducing the potential for costly penalties.

Supply Chain Security Review
A merger or acquisition often involves integrating new supply chains, which can expose your organization to significant cybersecurity risks. Our Supply Chain Security Review evaluates the security posture of the acquired company’s third-party vendors and suppliers. We assess the risk management policies, security controls, and data protection practices of all third parties involved in the transaction. By identifying vulnerabilities in the supply chain, we help mitigate risks that could compromise your security, integrity, and operational continuity. This thorough evaluation ensures that your newly combined organization’s supply chain is secure, resilient, and free from external threats that could disrupt business post-acquisition.

Security Program Development
Following a merger or acquisition, it’s essential to unify and strengthen security practices across both organizations. Our Security Program Development service helps integrate the security programs of both companies into a cohesive, company-wide strategy. We work with you to standardize policies, procedures, and security protocols that align with the goals of the newly merged entity. This includes revisiting risk management, access control, incident response, and employee training to ensure a smooth transition. By implementing a robust and unified security program, we help safeguard your new, expanded organization from evolving threats and ensure that security remains a priority throughout the integration process.

Enterprise Security Strategy Consulting
Mergers and acquisitions present the perfect opportunity to evaluate and strengthen your organization’s enterprise security strategy. Our Enterprise Security Strategy Consulting focuses on aligning the security objectives of the newly merged companies. We work closely with your leadership teams to assess the existing security infrastructures, identify gaps, and develop a unified, future-proof strategy. From risk assessments to incident response planning, we ensure that your organization has a comprehensive strategy to address internal and external threats. By enhancing your security framework, we help ensure that your newly merged entity is resilient against cyberattacks, data breaches, and operational risks.

Cyber Insurance Audit
A merger or acquisition often triggers a reassessment of your organization’s cybersecurity posture, including your insurance coverage. Our Cyber Insurance Audit evaluates your existing cyber insurance policies, helping to ensure they adequately cover the new, expanded organization’s risk profile. We perform a thorough review of the acquiring company’s and target company’s insurance coverage, ensuring that both organizations are aligned on risk management and that gaps are identified and addressed. By ensuring your organization has comprehensive, appropriate cyber insurance coverage, we help protect against potential financial losses resulting from cyber incidents, business interruptions, or legal liabilities post-merger.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
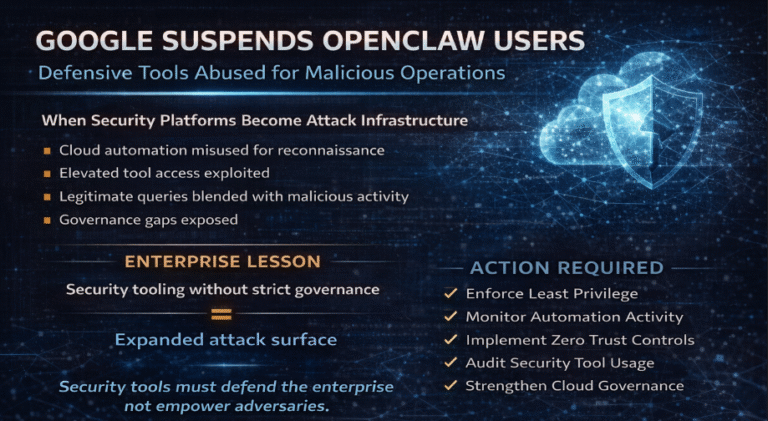
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…