Center of Excellence Security - Blockchain Infra Audits
Fortify Your Blockchain Backbone!
We audit consensus protocols, nodes, wallets, and bridges to eliminate weak links across your blockchain infrastructure.
Blockchain Infra Audits at COE Security

COE Security’s Security Audits for Blockchain Infrastructure delivers comprehensive evaluations of your full blockchain ecosystem – from node configurations and consensus layers to APIs, key management, and relay systems. We combine configuration analysis, network penetration testing, and protocol emulation to simulate real-world threats and ensure your infrastructure resists Sybil, Eclipse, and RPC-based attacks. Scheduled assessments or post-update audits help your team identify misconfigurations and harden infrastructure before it becomes a liability. You receive prioritized findings and implementation-level guidance to secure nodes, bridge operations, consensus logic, and cloud infrastructure. Continuous environment coverage across private and public chains comes with expert validation, supply chain review, and alignment with regulatory frameworks and best practices.
Our audits also evaluate resilience against network partitioning, DoS vectors, and chain-specific vulnerabilities, ensuring both operational continuity and stakeholder trust. We help teams build robust, scalable, and compliant blockchain systems with security baked into every layer.
Our Approach
Identify the infrastructure components including blockchain nodes, validators, bridges, APIs, wallets, and orchestration systems.
Set up a controlled test environment that replicates production deployment for accurate infrastructure-level testing.
Enumerate and validate configurations such as firewalls, key stores, consensus settings, and runtime permissions.
Develop a tailored threat model specific to the infrastructure and use case, accounting for consensus-layer risks, peer-to-peer exposure, and external services.
Execute penetration testing against API endpoints, internal admin panels, exposed ports, and connected systems.
Assess node and wallet hardening, reviewing authentication schemes, patch levels, SSL/TLS configurations, and access control policies.
Evaluate encryption protocols and data flows, verifying that all communication and storage comply with security best practices.
Review monitoring, logging, and alerting capabilities to ensure effective incident detection and response.
Compile a detailed infrastructure audit report with prioritized findings and implementation-specific security recommendations.
Support remediation and revalidation, assisting your DevOps and security teams in fixing issues and confirming their resolution.
Node-Level Assessment
Protocol Attack Simulation
Key & API Security
Deployment Hardening
Blockchain Infra Auditing Process
Our established blockchain infra audit methodology delivers comprehensive testing and actionable recommendations.
Architecture Analysis
Threat Modeling
Configuration & Network Testing
Protocol & Service Abuse Simulation
Reporting
Why Choose COE Security’s Blockchain Infra Audit?
Full-Stack Coverage – Assess nodes, APIs, RPC endpoints, wallets, key management, and backend systems.
CIS Benchmarking – Align infrastructure with industry standards and secure configurations.
Cloud-to-Chain Security – Audit blockchain hosting environments across AWS, Azure, GCP, etc.
Zero Trust Enforcement – Identify and fix architectural weaknesses in access controls.
Exploit Simulation – Simulate known attack vectors like Eclipse attacks, Sybil attacks, and more.
End-to-End Threat Modeling – Map all potential threat surfaces and lateral movement paths.
Private Key Security Assessment – Secure seed storage, key usage policies, and key rotation mechanisms.
Compliance Alignment – Address security mandates under GDPR, ISO 27001, and Crypto AML regulations.
Attack Surface Minimization – Reduce the number of exploitable entry points with security-first redesign suggestions.
Ongoing Risk Intelligence – Stay updated with threat reports tailored to your infrastructure profile.
Five Areas Section of Blockchain Infra Audits

Crypto Blockchain Security
Our Crypto Blockchain Security service focuses on securing blockchain-based platforms, cryptocurrencies, and decentralized ecosystems. We perform deep assessments on wallets, nodes, consensus protocols, and DeFi components to uncover vulnerabilities such as flash loan exploits, private key leakage, and oracle manipulation. We also evaluate token logic, cryptographic integrity, and operational controls. By simulating real-world threats and analyzing internal architecture, we help prevent attacks that target core blockchain components. Whether you’re launching a new protocol or operating at scale, this service ensures your platform is resilient against both technical exploits and strategic economic manipulation.
Cloud Security Penetration Testing
Most blockchain infrastructures are cloud-hosted or hybrid in nature, which makes cloud security vital. Our Cloud Security Penetration Testing service evaluates AWS, Azure, GCP, and other platforms for misconfigurations, privilege escalations, exposed endpoints, and weak IAM policies. We simulate attacks on cloud services that host blockchain nodes, APIs, explorers, and smart contract engines. This includes VPC security, storage configurations, container workloads, and CI/CD pipelines. Our objective is to detect exploitable vulnerabilities that could lead to service disruption, data leakage, or infrastructure compromise-ensuring your blockchain environment is secure at both the application and infrastructure levels.

Network Penetration Testing
Blockchain networks rely heavily on peer-to-peer communication and distributed consensus, making them uniquely exposed to network-layer threats. Our Network Penetration Testing service identifies risks such as open ports, misconfigured firewalls, man-in-the-middle attack vectors, and unencrypted traffic. We test internal and external infrastructure—nodes, relayers, RPC endpoints, and validator communications—for weaknesses that could enable traffic manipulation, denial of service, or unauthorized access. We also validate your network segmentation and latency resilience to ensure robust, uninterrupted consensus. This service ensures your blockchain infrastructure is protected against both external attackers and insider threats at the network level.

Application Security Consulting
Our Application Security Consulting service supports blockchain teams in building secure, scalable applications from the ground up. We help design secure APIs, architecture patterns, access controls, and validator logic. Our team works with developers to enforce strong authentication models, data validation pipelines, and runtime protections across node interfaces, explorers, wallets, and chain management dashboards. We also provide guidance on securing communication protocols, RPC methods, and integrations with third-party platforms. This proactive consulting ensures blockchain infrastructure applications are robust against common and complex threats-bridging the gap between development speed and long-term security assurance.

Supply Chain Security Review
Blockchain infrastructures often rely on multiple third-party components—open-source libraries, external oracles, hosted node services, and integrated APIs. Our Supply Chain Security Review assesses the security posture of every external dependency. We identify outdated libraries, compromised packages, shadow IT risks, and unverified updates that could compromise your infrastructure. We also examine the build pipeline, code repositories, and deployment artifacts to ensure secure delivery. By reviewing your software and infrastructure supply chain, we help eliminate hidden risks and ensure your blockchain operations are not vulnerable to indirect attacks or dependency abuse.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
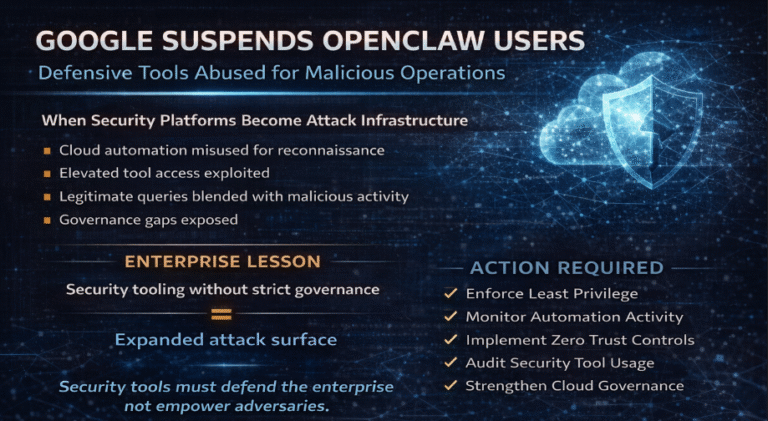
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…