Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
Gain real-time visibility, actionable insights, and comprehensive control over your application’s security posture with our expert solutions.
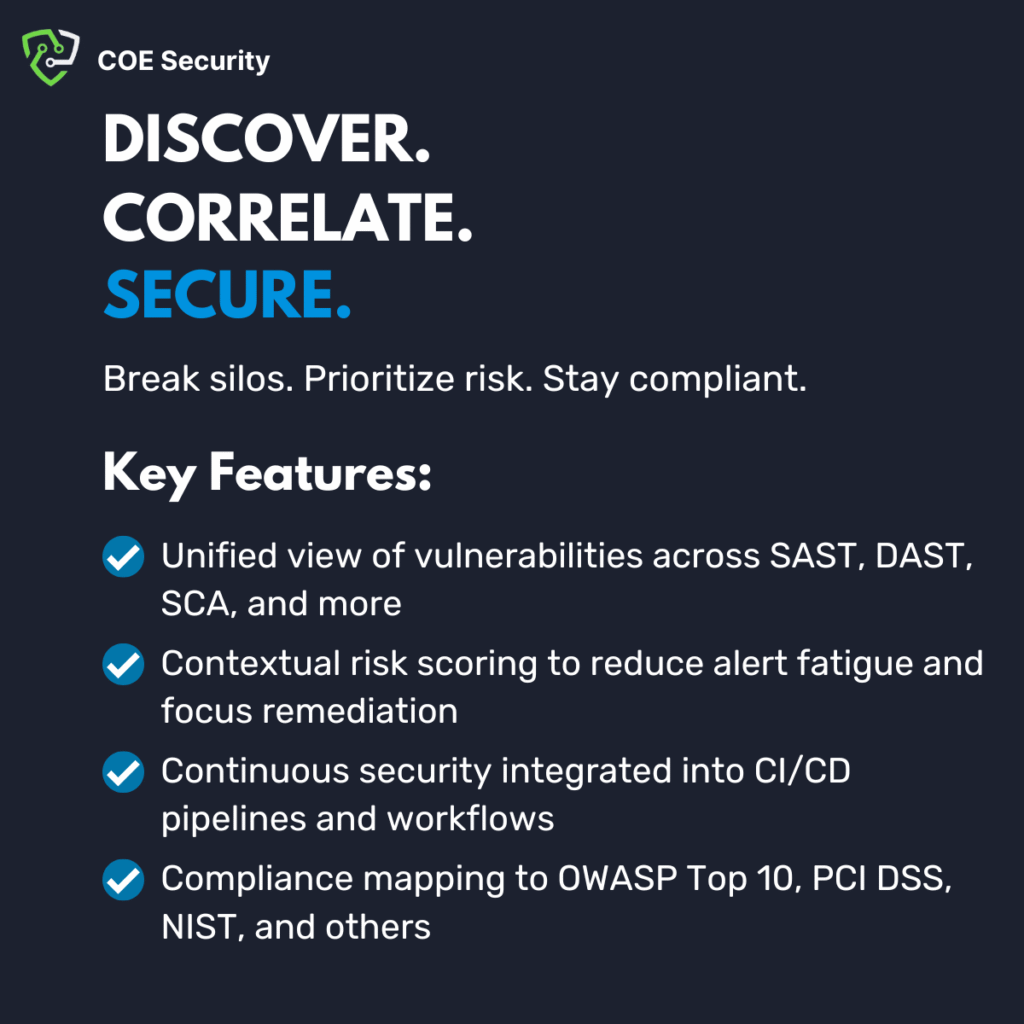
At COE Security, our Application Security Posture Management (ASPM) service helps organizations maintain continuous visibility and control over the security of their applications across development, testing, and production environments. As application ecosystems grow more complex, managing security posture across cloud-native, third-party, and internal applications becomes vital for risk reduction and regulatory compliance.
ASPM unifies signals from various security tools – such as SAST, DAST, SCA, and container security – into a centralized platform. We correlate findings, prioritize risks based on context, and deliver actionable insights to streamline remediation. This helps development and security teams collaborate effectively without slowing down agile workflows or DevOps pipelines.
With COE Security’s ASPM, you gain a dynamic, risk-aware view of your application landscape, empowering you to make smarter decisions and proactively protect against evolving threats.
Define ASPM Objectives and Scope: Establish clear goals and define the scope across development, testing, and production environments to ensure full lifecycle visibility of application security.
Integrate Security Tools Across Pipeline: Connect tools like SAST, DAST, SCA, and container scanners into CI/CD pipelines to centralize security signals from multiple sources.
Build a Unified Application Inventory: Maintain a live inventory of all applications, APIs, services, and components to track their security posture continuously.
Correlate and Deduplicate Findings: Use intelligent correlation to eliminate duplicate findings and connect vulnerabilities across tools, layers, and development stages.
Prioritize Risks Contextually: Assess and rank vulnerabilities based on exploitability, asset value, environment exposure, and business impact for smarter decision-making.
Map to Security and Compliance Standards: Align findings with frameworks like OWASP Top 10, NIST, PCI DSS, and ISO 27001 to ensure regulatory and best-practice compliance.
Enable Developer-Centric Security Feedback: Deliver actionable security insights directly to developers in real time through IDEs, pull requests, and build notifications.
Automate Remediation Workflows: Streamline the resolution of vulnerabilities by automating ticket creation, patch workflows, and security playbooks within existing tools.
Continuously Monitor Posture Changes: Track drift in application security posture over time, using dashboards and alerts to detect regressions or emerging risks.
Report Security Metrics to Stakeholders: Generate customized reports that show risk posture, remediation trends, and compliance alignment to leadership and auditors.
Full Lifecycle Visibility: We provide end-to-end visibility of application risks from development to deployment, empowering proactive decision-making.
Centralized Security Intelligence: COE Security unifies signals from all major AppSec tools into one dashboard for streamlined analysis and action.
Risk-Based Vulnerability Prioritization: Our contextual approach ensures critical issues are addressed first, saving time and reducing breach exposure.
Seamless DevSecOps Enablement: We embed ASPM into CI/CD workflows, allowing security checks without slowing down agile development cycles.
Developer-Friendly Remediation: We integrate directly with developer tools to provide precise, timely, and contextual fix recommendations.
Compliance Made Simple: Our platform maps vulnerabilities to compliance standards and generates reports that simplify audits and governance.
Smart Correlation and Deduplication: We reduce alert fatigue and noise by correlating and deduplicating findings across multiple tools and stages.
Scalable and Cloud-Native: COE Security’s ASPM supports hybrid and cloud-native environments, making it scalable across modern architectures.
Live Application Inventory: We provide a dynamic view of all in-use applications, components, and services, continuously updated for accuracy.
Proven ASPM Expertise: With deep experience in application security, COE Security ensures your organization maintains a strong and adaptive security posture.
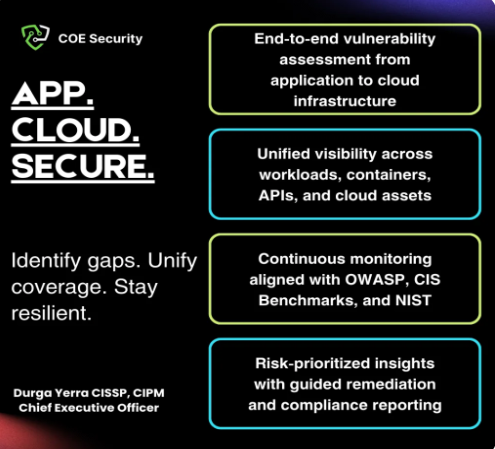
At COE Security LLC, our App-to-Cloud Vulnerability Management service bridges the security gaps between applications and their cloud environments. We conduct comprehensive assessments to identify vulnerabilities across application architectures, APIs, and cloud infrastructures, ensuring seamless integration without exposing critical assets. Our approach includes real-time risk monitoring, compliance alignment, and automated remediation, addressing misconfigurations, weak access controls, and insecure data flows. With tailored strategies and advanced tools, we help you maintain a robust security posture. Partner with COE Security to safeguard your application-to-cloud ecosystem against evolving cyber threats while ensuring operational continuity.

At COE Security LLC, our Managed Security Intelligence & Awareness service is designed to provide organizations with a proactive defense against evolving cyber threats. By combining real-time threat intelligence, behavioral analysis, and security awareness training, we equip your team to recognize and respond to risks effectively. Our experts deliver customized phishing simulations, policy updates, and incident response playbooks to enhance resilience against human-centric vulnerabilities. With continuous monitoring and tailored insights, we ensure your organization stays informed and prepared. Partner with COE Security to foster a security-aware culture and safeguard your operations against emerging challenges.

At COE Security LLC, our Virtual Chief Information Security Officer (vCISO) services provide organizations with expert guidance to develop, manage, and enhance their cybersecurity strategies. Our vCISO offering includes risk assessments, policy development, compliance alignment, and incident response planning, ensuring a comprehensive approach to security. Acting as a trusted advisor, our vCISO collaborates with your leadership to align security initiatives with business objectives, addressing challenges like regulatory adherence, threat management, and workforce training. With COE Security’s vCISO services, you gain cost-effective access to top-tier cybersecurity expertise, empowering your organization to stay resilient in an evolving threat landscape.

At COE Security LLC, our Corporate Application Security Training equips development teams with the knowledge and skills to build secure applications. Our programs focus on industry best practices, covering topics like OWASP Top 10 vulnerabilities, secure coding techniques, and threat modeling. Delivered through customized workshops, hands-on labs, and real-world scenarios, our training ensures developers can identify and mitigate risks effectively. By fostering a security-first mindset, we help organizations reduce vulnerabilities, improve compliance, and enhance the resilience of their applications. Partner with COE Security to empower your teams and safeguard your corporate applications.

At COE Security LLC, our Secure Software Development Consulting services help organizations integrate security into every phase of the software development lifecycle. We provide expert guidance on secure coding practices, threat modeling, and vulnerability management, ensuring your software is resilient against evolving cyber threats. Our consultants work closely with development teams to implement DevSecOps principles, automate security testing, and establish compliance with industry standards. By embedding security early, we reduce risks, lower costs, and accelerate delivery. Partner with COE Security to build robust, secure software that meets both business goals and regulatory requirements.
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Certified cybersecurity professionals you can trust.
Testing aligned with OWASP, SANS, and NIST.
Clear reports with practical remediation steps.















As digital transformation accelerates, electronic signatures have become a core part of…
In a proactive security move, Google has suspended a number of OpenClaw…
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…