Center of Excellence Security - Smart Contract Audits
Secure Your Smart Contracts with Proven Precision!
From logic validation to formal methods, we ensure your blockchain contracts are error-free, exploit-resistant, and built to last.
Smart Contract Audits at COE Security

COE Security’s Blockchain Contract Audits & Formal Verification offers rigorous,end-to-end analysis of smart contract code to ensure business logic correctness and airtight security. Using a combination of static analysis, symbolic execution, and mathematical proof techniques, we uncover hidden flaws – such as reentrancy, integer overflow, and logic loopholes – as well as formally verify that contracts execute as intended. Our service supports repeatable audits after each code release and before deployment, helping teams catch issues early and reduce rework. You’ll receive prioritized findings and detailed fix recommendations to secure token logic, governance mechanisms, and financial flows. Continuous contract coverage and version visibility are paired with automated tools, expert reviews, and developer-friendly guidance to maintain integrity across platforms like Ethereum, Solana, and private EVM chains.
We simulate adversarial conditions to test contract behavior under stress. From DeFi to enterprise tokenization, our solutions ensure secure and reliable on-chain interactions.
Our Approach
Define the audit scope by identifying the contracts, libraries, and protocol logic involved, along with business logic and expected behaviors.
Create an isolated testing environment to deploy and interact with the smart contracts safely without affecting production systems or live assets.
Perform automated vulnerability scanning using industry-standard tools to quickly detect known security issues such as reentrancy, integer overflow, and access control flaws.
Conduct a thorough manual review of contract code to identify logic vulnerabilities, hidden dependencies, and misaligned incentive structures.
-
Apply formal verification methods where applicable by modeling contract behavior in a formal language and mathematically verifying it against desired properties.
-
Develop proof-of-concept (PoC) exploits to validate critical findings and demonstrate real-world attack scenarios.
-
Analyze business logic alignment by comparing code behavior with client specifications, functional requirements, and economic assumptions.
-
Deliver a comprehensive report detailing vulnerabilities, impact levels, and step-by-step remediation guidance for developers.
-
Retest remediated code to ensure all critical issues have been resolved and no regressions are introduced.
Code-Guided Review
Logic & Permission Checks
Formal Proof Validation
Security Simulation
Smart Contract Auditing Process
Our established thick client penetration methodology delivers comprehensive testing and actionable recommendations.
Code Review
Threat Modeling
Automated & Manual Testing
Formal Verification
Reporting
Why Choose COE Security’s Smart Contract Audit?
Zero-Day Protection – Identify logic flaws and vulnerabilities before attackers can exploit them.
Mathematical Rigor – Formal verification ensures smart contracts behave exactly as intended, leaving no room for ambiguity.
Prevention of Financial Loss – Catch critical bugs that could lead to asset lockups or unauthorized fund transfers.
Compliance Assurance – Meet the highest security standards for DeFi, token issuance, and enterprise contracts.
Custom Risk Scoring – Get a vulnerability severity breakdown for prioritized remediation.
Code-to-Spec Validation – Ensure smart contract code aligns with business requirements and documentation.
Audit Trail Transparency – Deliver complete documentation for investor and regulatory reporting.
Trusted by Protocols – Experience with major platforms like Ethereum, Solana, BNB Chain, and more.
Static and Dynamic Analysis – Combine multiple scanning methods for comprehensive detection.
Post-Audit Support – Free retesting and advisory for secure post-launch deployment.
Five Areas Section of Smart Contract Audits

API Penetration Testing
APIs are critical to modern applications but are also frequent targets for attackers. Our API Penetration Testing service rigorously assesses REST, GraphQL, and WebSocket APIs for vulnerabilities such as broken authentication, injection flaws, data exposure, and improper access controls. By simulating real-world attacks, we evaluate endpoint resilience, validate request/response behaviors, and uncover logic flaws or misconfigurations that could lead to data breaches or service disruptions. Our testing methodology aligns with OWASP API Security Top 10 and industry best practices. We deliver detailed reports and remediation guidance, enabling secure API integration across mobile, web, and enterprise systems.
Product Penetration Testing
COE Security’s Product Penetration Testing service evaluates the security of an entire digital product ecosystem, including web frontends, mobile applications, backend infrastructure, authentication systems, and third-party integrations. We take a holistic approach to uncover vulnerabilities that arise from interactions between components, such as chained exploits, misconfigured endpoints, or business logic flaws. This end-to-end assessment mimics real-world attacker behavior and tests the resilience of the entire user experience. Our testing covers everything from session management to data storage and access control, ensuring your product is secure across all layers. Post-assessment, we provide actionable insights to strengthen your overall security posture.

Software Compliance Testing
Compliance with industry standards and regulations is essential, even for thick client applications. Our Software Compliance Testing service ensures that your thick client applications meet the required regulatory frameworks, including GDPR, HIPAA, PCI-DSS, and others. We conduct detailed assessments to ensure that your software adheres to security, data privacy, and accessibility standards. By performing thorough compliance testing, we help you identify any gaps or non-compliance areas that could lead to penalties, data breaches, or reputational damage. Our testing provides you with the assurance that your thick client application meets legal and regulatory requirements, minimizing legal and operational risks.

Crypto Blockchain Security
COE Security’s Crypto Blockchain Security service is tailored to protect decentralized ecosystems from evolving threats. We perform deep technical assessments of cryptocurrency platforms, wallets, consensus mechanisms, DeFi infrastructures, node security, and cross-chain bridges. Our team investigates common and emerging risks such as private key leakage, oracle manipulation, replay attacks, and flash loan exploits. We also validate cryptographic implementations, token security, and transaction workflows to detect and mitigate weaknesses. Our threat modeling approach is designed for both permissioned and permissionless environments. By securing the foundational layers of blockchain platforms, we help ensure operational integrity, user trust, and long-term ecosystem resilience.

Application Security Posture Management
Application Security Posture Management is a continuous, proactive approach to managing and improving the security of your thick client applications. We help you monitor your application’s security posture over time, ensuring that new vulnerabilities are quickly identified and mitigated. This includes regular vulnerability assessments, patch management, and threat intelligence integration to stay ahead of emerging threats. Our team provides ongoing support to address security gaps, track the effectiveness of security controls, and ensure that your application’s security posture is always up to date. By maintaining a strong security posture, we help you protect your thick client applications from evolving cyber threats.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
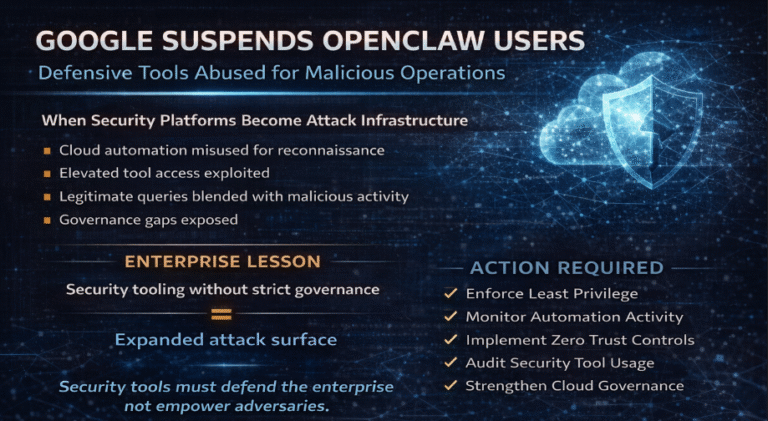
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…