Resilient Data Security Architecture in 2026
In 2026, data security has evolved into a strategic enterprise mandate. Organizations…
Building resilience into every stage of your software development lifecycle.
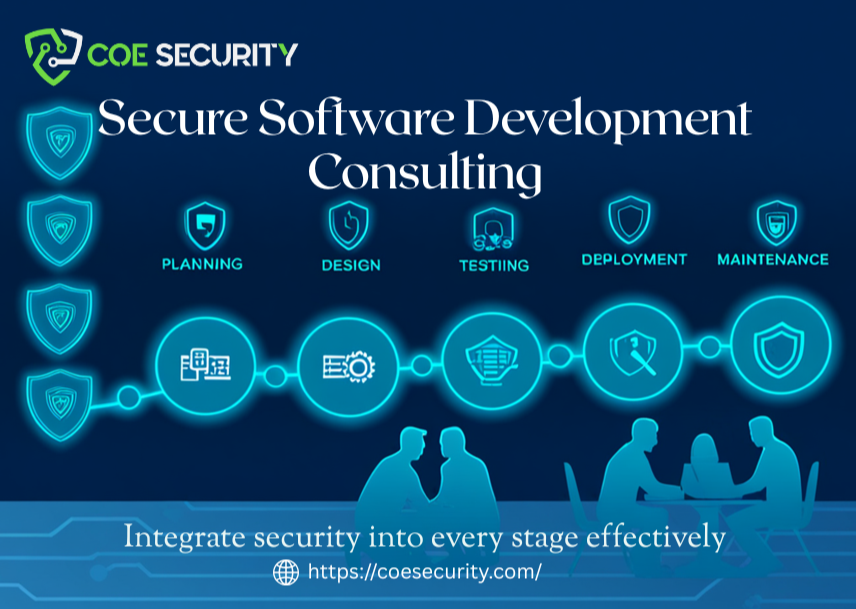
COE Security’s SSDLC services integrate security throughout your software development lifecycle, helping you build secure applications from the ground up. By embedding security into design, development, and deployment phases, we identify vulnerabilities early and reduce risk before release.
Our approach combines static code analysis, dynamic testing, manual reviews, and adversary simulation to uncover flaws that automated tools might miss. We deliver actionable, architecture-aware remediation guidance, ensuring alignment with your development goals and regulatory requirements.
Working closely with your teams, we foster a security-first mindset, enabling you to build resilient, compliant applications that can withstand evolving cyber threats. Our SSDLC consulting helps you shift left on security – saving costs, protecting data, and strengthening your software’s defense posture.
Tailored code reviews and threat modeling combined with expert penetration testing, real‑time vulnerability reporting, and prioritized remediation plans - hardening your software, reducing exploit risk, and ensuring secure release cycles.
On‑demand secure‑by‑design guidance, developer training, and automated SAST/DAST integration - embedding security into every sprint, minimizing coding flaws, and accelerating compliant delivery.
End‑to‑end security control deployment with expert configuration, continuous monitoring, and automated policy enforcement - ensuring robust defenses, seamless integration, and reduced implementation overhead.
Continuous asset discovery and risk scoring with real-time posture dashboards, expert tuning, and adaptive policy updates - maintaining visibility, prioritizing fixes, and strengthening your security baseline.
On‑demand instructor‑led and micro‑learning modules with scenario‑based exercises, automated compliance tracking, and expert feedback - building staff competence, ensuring policy adherence, and strengthening your first line of defense.
On-demand static and dynamic smart contract analysis with scenario-based test cases, automated vulnerability detection, and expert validation - ensuring code integrity, preventing exploits, and strengthening trust in decentralized applications.
On-demand instructor-led and micro-learning modules with scenario-based code review labs, secure-coding best-practice drills, automated progress tracking, and expert debriefs - empowering development teams, embedding security culture, and fortifying your application development pipeline (SDLC).
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Certified cybersecurity professionals you can trust.
Testing aligned with OWASP, SANS, and NIST.
Clear reports with practical remediation steps.















In 2026, data security has evolved into a strategic enterprise mandate. Organizations…
A recent security challenge offering a reward exceeding ten thousand dollars to…
As digital transformation accelerates, electronic signatures have become a core part of…