Parrot OS 7.0

Parrot OS 7.0 is not a routine Linux upgrade. It is a full system rewrite designed for the realities of modern security testing. For penetration testers, red teams, security consultants, and enterprise labs, this release marks a baseline shift in how offensive and defensive security environments are built and maintained. This is not about new […]
MongoDB Vulnerability

A newly disclosed vulnerability in MongoDB highlights a dangerous and often underestimated class of risk: unauthenticated memory disclosure. Tracked as CVE-2025-14847, this flaw allows attackers to extract sensitive server memory without credentials, alerts, or obvious signs of compromise. For organizations running exposed MongoDB instances, the risk is immediate and real. This is not a denial-of-service […]
Controls Become the Exploit

AI safety dialogs are designed to protect users from dangerous actions.A newly identified attack technique shows how that very protection can be turned into an execution path for malicious code. The technique, known as Lies-in-the-Loop, exposes a fundamental weakness in how AI code assistants implement human approval workflows. Any organization relying on AI-assisted development should […]
University of Sydney Data Breach

The University of Sydney data breach did not involve a sophisticated zero-day exploit. There was no advanced malware or nation-state capability on display. Instead, thousands of personal records were exposed because of something far more common—and far more dangerous: a forgotten system. Hackers accessed a legacy IT code library used for software development. Inside it […]
AI-Assisted Vulnerability Discovery

The pace of software development has accelerated dramatically over the last decade, driven by cloud-native architectures, microservices, continuous deployment, and the growing adoption of AI across business functions. While these advances have enabled organizations to innovate faster, they have also introduced unprecedented complexity into modern applications. Codebases are larger, dependencies are deeper, and the attack […]
Hypothesis-Driven Penetration Testing

Penetration testing is evolving. As applications grow more complex, traditional approaches built around broad scanning and manual reconnaissance are increasingly inefficient. Modern environments span APIs, cloud-native architectures, client-side logic, and third-party integrations. While tooling has advanced, much of a pentester’s time is still spent identifying where to look rather than validating what actually matters. This […]
Fake Shopping Domains Surge

As the 2025 holiday shopping season accelerates, threat actors are exploiting consumer urgency at scale. A sharp increase in fraudulent shopping domains is targeting online buyers searching for discounts, flash sales, and limited time offers. This activity is not opportunistic or isolated. It is coordinated, automated, and designed to move faster than traditional detection and […]
BlindEagle Email Campaign

Email security frameworks have matured significantly over the past decade. SPF, DKIM, and DMARC are now widely deployed and effective at stopping impersonation and spoofing from external attackers. Yet recent activity attributed to the BlindEagle threat group highlights a growing weakness that technical controls alone cannot address: misplaced trust in internal systems. This campaign demonstrates […]
Containment Is Not the End of the Incident
On December 15, 2025, SoundCloud confirmed unauthorized access to user data affecting approximately 20% of its global user base. The attackers exfiltrated email addresses and public profile information. Importantly, no passwords, authentication secrets, or financial data were compromised. From a narrow technical perspective, this distinction matters. It prevented immediate account takeover, direct financial fraud, and […]
SYSTEM-Level Code Execution
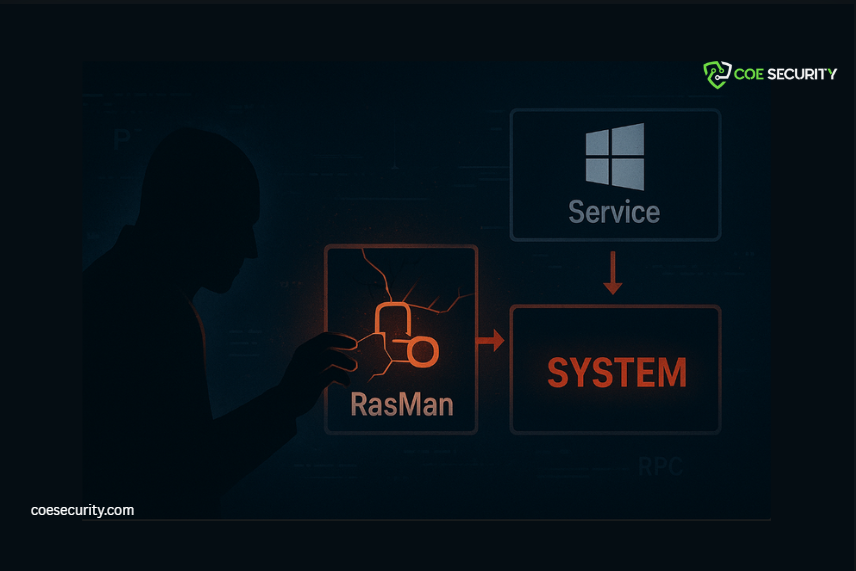
A critical weakness has been identified in Windows Remote Access Connection Manager (RasMan) that enables local attackers to achieve SYSTEM-level code execution. What makes this issue especially dangerous is not a single vulnerability-but a chained exploitation technique that breaks long-standing Windows security assumptions. Executive Summary Impact: Full local privilege escalation to NT AUTHORITY\SYSTEM Attack Type: […]
