Gmail Phishing: Rising Threat

Phishing remains one of the most dangerous and effective cyber threats, and Gmail users are increasingly becoming prime targets. Recently, cybersecurity researchers have uncovered a sophisticated Gmail phishing campaign designed to steal login credentials and compromise user trust. These attacks rely on deceptive emails crafted to appear authentic, often leveraging urgent prompts to trick users […]
APT Hits Taiwan’s Web Core
A sophisticated threat group known as UAT-7237 has been linked to a large-scale cyber campaign breaching Taiwanese government and educational web servers. This Chinese-speaking APT, believed to be a subgroup of UAT-5918, has been active since at least 2022 and is now using heavily modified open-source hacking tools to carry out highly targeted attacks. Attack […]
WinRAR Zero-Day Hit by RomCom

A critical security flaw in WinRAR, tracked as CVE-2025-8088, is under active exploitation by the Russia-linked hacking group RomCom. The vulnerability allows malicious .rar archives to extract files into unintended system paths-such as the Startup folder-leading to automatic malware execution upon reboot. Because WinRAR does not have an auto-update function, this flaw remains a significant […]
Unicode Deception Bypasses URL Trust
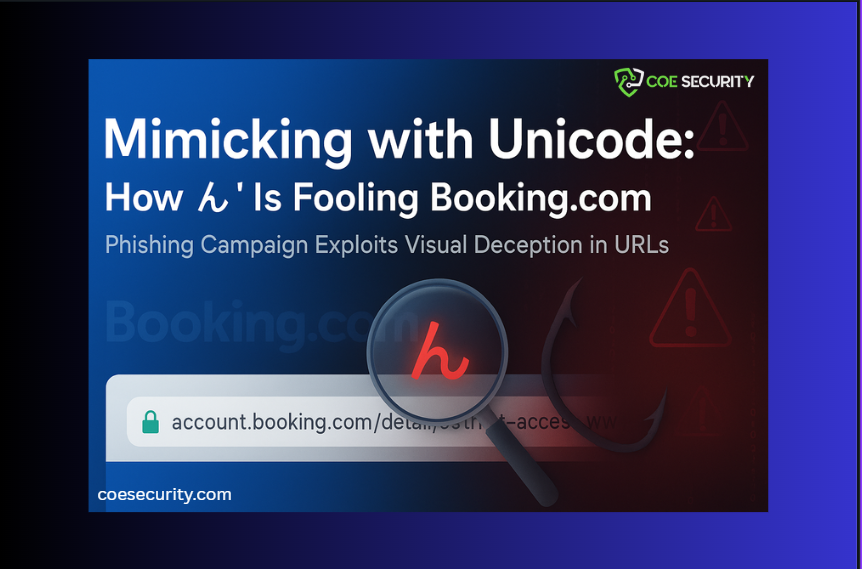
A new phishing campaign has emerged that uses the Japanese hiragana character ん to impersonate forward slashes in website URLs. This subtle trick creates the illusion of a legitimate domain while quietly directing victims to malicious sites. How the Attack Works Instead of a forward slash / in URLs, attackers insert the ん character, which […]
Stealthy Android Banking Malware

Cybersecurity researchers have identified PhantomCard, a dangerous Android banking trojan that abuses near-field communication (NFC) technology to execute fraudulent transactions. This sophisticated malware campaign is currently targeting banking customers in Brazil, marking a significant escalation in mobile financial threats. How PhantomCard Works PhantomCard uses NFC relay techniques to bypass traditional banking authentication measures, allowing attackers […]
FortiWeb Auth Bypass Threat

A critical flaw (CVE-2025-52970) in Fortinet’s FortiWeb web application firewall has been discovered – one that allows unauthenticated remote attackers to impersonate any existing user on affected systems. This bypass stems from improper handling of cookie parameters during session validation and carries a high severity score of 7.7. FortiWeb versions 7.0–7.6 are affected, while version […]
RDP Flaw CVE-2025-32710 Risk

A newly uncovered vulnerability (CVE-2025-32710) in Windows Remote Desktop Services poses a high-risk threat to enterprise environments. This flaw-stemming from a use-after-free condition combined with a race condition-enables unauthenticated attackers to execute arbitrary code remotely with no need for user interaction. The affected systems include multiple versions of Windows Server and RDS deployments. What Makes […]
VMware ESXi Bug Puts 17K Servers at Risk

A critical integer-overflow vulnerability, CVE-2025-41236, has been discovered in VMware ESXi’s HTTP management interface, earning a CVSS score of 9.3. Affected versions include ESXi 7.x and several 8.x builds. This flaw enables unauthenticated remote attackers to execute arbitrary code, escalate privileges, or deploy ransomware, placing virtual infrastructures at significant risk. Despite public advisories, recovery has […]
Curly Comrades Cyber Spy Threat

In a recent wave of cyberattacks, a threat actor group known as Curly Comrades has been identified targeting government organizations across multiple regions. These attackers deploy sophisticated custom malware to infiltrate systems, steal sensitive data, and evade detection through advanced obfuscation techniques. The campaign involves spear-phishing emails and malicious attachments designed to compromise systems running […]
Jenkins Git Param RCE Threat

A serious command injection flaw (CVE-2025-53652) in the Jenkins Git Parameter plugin has emerged as a critical risk to DevOps environments. Originally rated medium severity, researchers found the flaw enables remote code execution (RCE) through unchecked user-defined Git parameters that get executed in shell commands. Approximately 15,000 internet-facing Jenkins servers lack authentication, making them highly […]
