Center of Excellence Security - Remote Work Security Assessment
Secure Your Remote Workforce with Confidence!
Assess your remote work environment, fortify your defenses, and empower your team with expert security insights.
Remote Work Security Assessment Solutions
At COE Security, we offer Remote Work Security Assessments to help organizations secure their distributed workforce and reduce the risks associated with remote access, unsecured devices, and home networks. As remote and hybrid work models become the norm, it’s critical to ensure that employees can work securely from any location without compromising your organization’s security posture.
Our assessment identifies vulnerabilities in remote work setups, evaluates endpoint protections, access controls, data handling practices, and the use of collaboration tools. We ensure your remote work policies are effective, your technology stack is properly configured, and your workforce is trained to recognize threats like phishing and social engineering attacks.
COE Security’s remote work assessments are designed to give you visibility into your remote environment, enforce security standards, and ensure your organization remains resilient even beyond the traditional office perimeter.
Our Approach
Define assessment scope and workforce model: Identify remote roles, tools, devices, and cloud services involved in daily operations.
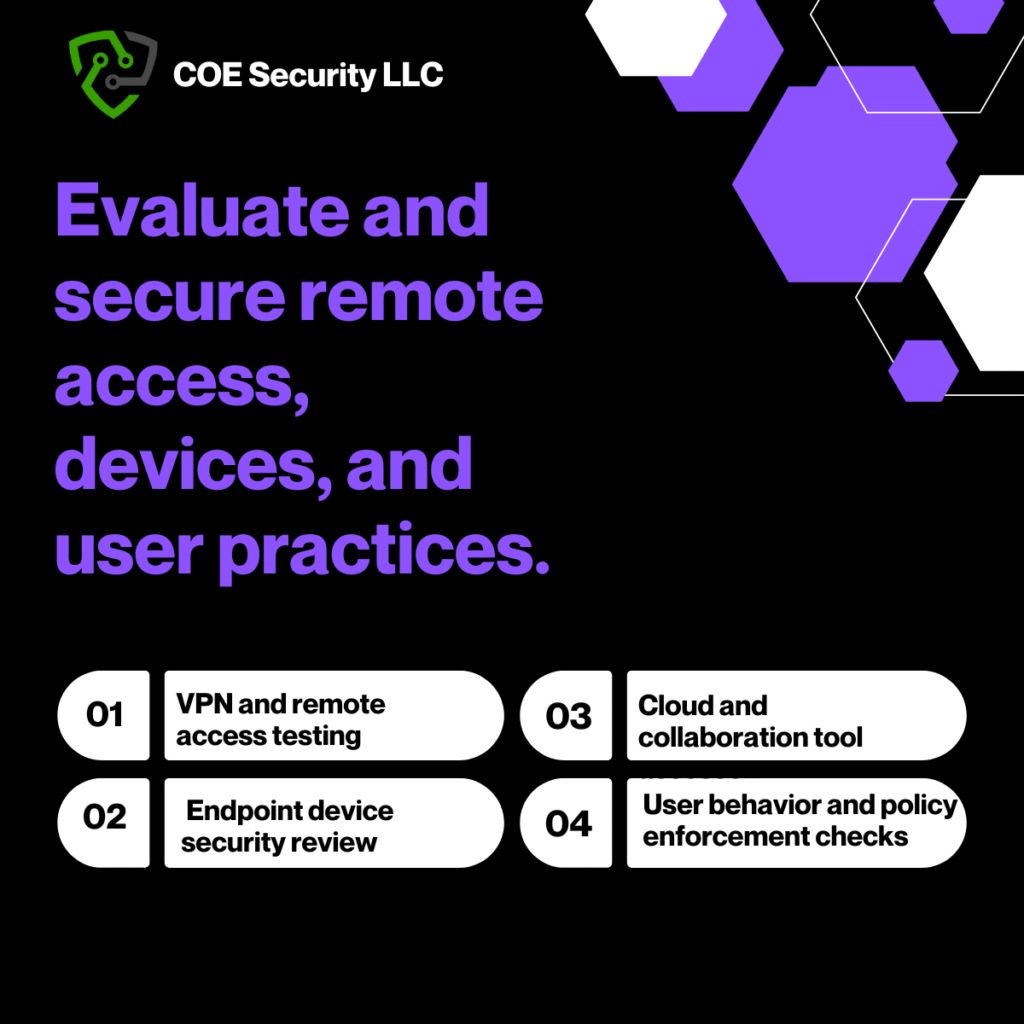
Review endpoint and device configurations: Evaluate employee laptops, mobile devices, and BYOD setups for security compliance.
Assess VPN and remote access solutions: Test for configuration flaws, weak encryption, split tunneling, and insecure access policies.
Validate multi-factor authentication controls: Ensure strong MFA is enforced across VPNs, SaaS platforms, and internal systems.
Analyze collaboration and communication tools: Examine tools like Zoom, Slack, Teams for exposure, access control, and data leaks.
Test cloud access and privilege management: Evaluate identity and access management (IAM) policies for least privilege enforcement.
Inspect data handling and file-sharing practices: Review usage of cloud storage, email, and transfer tools for sensitive data leaks.
Evaluate monitoring and logging coverage: Determine visibility across remote assets for threat detection and incident response readiness.
Simulate phishing and social engineering attacks: Conduct real-world simulations to assess employee awareness and response behavior.
Report findings with tailored guidance: Deliver actionable recommendations to strengthen remote infrastructure and policies.
Endpoint Security Evaluation
Secure Remote Access Review
Cloud Security & Collaboration Tools Assessment
Network & Communication Security Analysis
Remote Work Security Assessment Process
Assess
Evaluate
Report
Recommend
Monitor
Why Choose COE Security’s Remote Work Security Assessment?
Built for hybrid and remote-first businesses: We help secure work-from-anywhere setups across cloud, mobile, and home networks.
End-to-end visibility of remote risk posture: We assess endpoints, cloud apps, network access, and user behavior comprehensively.
Human-centric threat simulation included: Our phishing and social tests uncover risks beyond technical controls or tools.
Expert analysis of common remote tools: We understand the risks in Slack, Teams, Zoom, Google Workspace, and Microsoft 365.
Zero trust and VPN architecture review: We evaluate the security of ZTNA, VPNs, and remote access gateways for best practices.
Support for compliance and governance needs: Our reports align with ISO 27001, NIST CSF, HIPAA, and industry regulations.
Practical device-hardening recommendations: We provide specific, tool-agnostic guidance for securing employee-owned devices.
CI/CD and remote DevOps security: We assess remote developer environments for secrets management and build system risks.
Fast deployment with minimal disruption: We conduct assessments remotely or hybrid, ensuring smooth operations during testing.
Used by regulated and tech-forward firms: We serve clients in healthcare, fintech, SaaS, and legal sectors managing remote risk.
Five areas of Remote Work Security Assessment

Application Security Consulting
At COE Security LLC, our Application Security Consulting services are tailored to help organizations safeguard their applications against vulnerabilities throughout the development lifecycle. We conduct comprehensive security assessments, including code reviews, vulnerability scans, and penetration testing, to identify and mitigate risks. Our experts integrate secure development practices such as OWASP guidelines, ensuring robust protection against threats like SQL injection, cross-site scripting, and authentication flaws. From design to deployment, we provide customized recommendations and training to strengthen your application’s security posture. Partner with COE Security to build resilient, compliant, and secure applications that instill user confidence.

API Penetration Testing
At COE Security LLC, our API Penetration Testing services focus on identifying vulnerabilities in APIs to protect critical data and ensure secure communication between systems. Using advanced testing methodologies, we assess API endpoints for weaknesses such as authentication flaws, improper data validation, and misconfigured permissions. By simulating real-world attack scenarios, we uncover security gaps that could expose sensitive information or disrupt operations. Following the assessment, we deliver detailed reports with actionable insights, empowering you to strengthen API security. Trust COE Security to safeguard your APIs and maintain the integrity and reliability of your digital ecosystem.

Cloud Security Consulting
At COE Security LLC, our Cloud Security Consulting services focus on empowering businesses to secure their cloud environments while maximizing efficiency and scalability. We assess cloud infrastructures, identify vulnerabilities, and implement tailored strategies to safeguard data, applications, and workflows. Our expertise spans multi-cloud, hybrid, and private cloud setups, ensuring compliance with industry standards like GDPR, HIPAA, and DPDPA. From secure cloud architecture design to continuous monitoring and incident response, we help organizations mitigate risks and enhance resilience. Partner with us to navigate the complexities of cloud security and achieve robust protection in an ever-evolving digital landscape.

Network Penetration Testing
At COE Security LLC, our Network Penetration Testing services focus on identifying vulnerabilities within your network infrastructure before malicious actors exploit them. Our experts simulate real-world attack scenarios to assess firewalls, routers, switches, and endpoints for potential weaknesses. Using industry-leading tools and methodologies, we uncover security gaps, including misconfigurations, outdated protocols, and insufficient access controls. After the assessment, we provide comprehensive reports with actionable recommendations to fortify your defenses. Trust COE Security to help you build a resilient network that withstands emerging threats and aligns with the highest security standards.

Compliance as a Service (CaaS)
At COE Security LLC, our Compliance as a Service (CaaS) offering helps organizations navigate complex regulatory landscapes with ease and confidence. We provide end-to-end compliance management, including gap assessments, policy development, and continuous monitoring aligned with standards such as GDPR, HIPAA, and DPDPA. Our experts deliver tailored frameworks to ensure your security controls meet legal and industry requirements. Through automated reporting, risk analysis, and employee training programs, we simplify compliance processes and reduce audit burdens. Partner with COE Security to maintain regulatory adherence, mitigate risks, and foster trust with customers and stakeholders.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
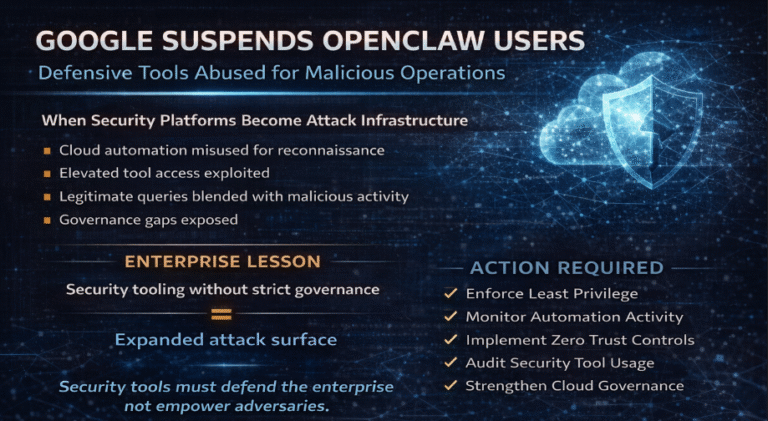
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…