Center of Excellence Security - Intellectual Property Risk Review
Protect Your Innovations with Uncompromising Vigilance!
Safeguard your intellectual assets, mitigate risks, and preserve your competitive edge with our expert IP risk review services.
Intellectual Property Risk Review at COE Security

At COE Security, our Intellectual Property (IP) Risk Review service helps organizations identify, assess, and mitigate risks to their critical intellectual assets such as proprietary software, algorithms, designs, and trade secrets. In today’s digital economy, IP is often the most valuable asset a company owns, making it a prime target for cyberattacks, insider threats, and inadvertent leaks during collaborations, product development, or mergers.
We work with product teams, legal departments, and cybersecurity leaders to evaluate how intellectual property is created, stored, accessed, and shared ensuring appropriate technical and administrative controls are in place to protect its confidentiality and integrity. Whether you’re a startup developing proprietary code or an enterprise managing patents and sensitive research, our service provides a structured and strategic approach to IP risk management.
Our Approach
Identify Critical Intellectual Property (IP) Assets: Catalog all key IP, such as patents, trademarks, trade secrets, and copyrights, to understand their value and importance to the organization.
Evaluate IP Ownership and Legal Protections: Review legal documentation and agreements to confirm ownership, ensuring IP is properly protected by relevant laws.
Assess Access Control and Security Measures: Evaluate how IP is accessed and protected within the organization, including file access rights, encryption, and secure storage practices.
Review Third-Party Relationships and Agreements: Assess contracts and agreements with third-party vendors, contractors, or partners to ensure that IP protection clauses are in place and upheld.
Examine Employee and Contractor IP Handling: Analyze how employees and contractors handle IP, ensuring confidentiality agreements, non-disclosure agreements (NDAs), and access protocols are in place.
Conduct a Risk Assessment of IP Systems and Infrastructure: Perform a security audit of the systems and infrastructure where IP is stored or used to identify vulnerabilities or risks.
Monitor IP Usage and Activity: Implement monitoring tools to detect unusual access, copying, or sharing of IP, identifying potential breaches or leaks.
Develop IP Protection and Risk Mitigation Strategies: Establish a set of strategies and practices for protecting IP, including cybersecurity measures, legal actions, and operational safeguards.
Create an IP Incident Response Plan: Develop a response plan for handling incidents of IP theft, misuse, or leakage, outlining immediate actions, legal steps, and communication protocols.
Review and Update IP Risk Management Practices: Regularly review and update IP risk management policies to account for evolving threats, technological changes, and legal updates.
Identify Critical Assets
Risk Assessment & Vulnerability Analysis
Tailored Risk Mitigation Strategy
Continuous Monitoring & Improvement
Intellectual Property Risk Review Process
Our established penetration testing methodology delivers comprehensive testing and actionable recommendations.
Assess
Analyze
Report
Remediate
Monitor & Optimize
Why Choose COE Security’s Intellectual Property Risk Review?
Comprehensive IP Risk Identification: We help identify and catalog all intellectual property assets, ensuring they are properly protected against potential threats.
Thorough Legal Compliance Review: We ensure that IP is fully compliant with relevant regulations and laws, reducing the risk of legal disputes or non-compliance.
Robust Access and Data Protection: Our review ensures that all IP is securely stored, with controlled access and strong encryption, preventing unauthorized use or theft.
Effective Third-Party Risk Management: We help assess and manage the risks posed by third-party vendors, ensuring that IP protection is included in contracts and agreements.
Employee and Contractor Awareness: We ensure that employees and contractors understand their responsibilities in protecting IP and adhere to non-disclosure and confidentiality agreements.
Real-Time Monitoring and Threat Detection: We implement advanced monitoring systems that provide continuous oversight of IP usage, enabling quick detection of potential breaches.
Tailored Risk Mitigation Plans: Our consultants provide actionable strategies to minimize IP risks, combining cybersecurity, legal, and operational approaches.
Dedicated Incident Response Plans: We offer comprehensive incident response plans for IP theft or misuse, ensuring swift containment and legal action if necessary.
Continuous Review and Improvement: We regularly assess and update IP risk management practices to keep pace with emerging threats and changing regulatory landscapes.
Expert IP Risk Management: With COE Security, you gain access to expert guidance on safeguarding your valuable intellectual property against both internal and external threats.
Five areas of Infrastructure Security

Legal Risk Review in New Territories
Expanding into new regions through mergers, acquisitions, or business growth introduces unique legal risks, particularly when it comes to intellectual property (IP) protection. Our Legal Risk Review in New Territories focuses on evaluating the legal landscape in the territories you’re entering to identify potential IP risks. We assess local IP laws, enforcement practices, and any regional variations in patent, trademark, and copyright protection. By identifying gaps in protection or jurisdictional issues, we help ensure that your IP assets are safeguarded in new markets, reducing the risk of infringement, legal disputes, or lost intellectual property during international expansion.

Compliance as a Service
IP protection must align with various regulatory frameworks across industries and regions. Our Compliance as a Service offering ensures that your IP strategy complies with the relevant laws and standards, whether local, national, or international. We help ensure that your IP processes, from creation to protection, follow best practices and comply with regulations like the General Data Protection Regulation (GDPR), industry-specific guidelines, and intellectual property laws. By embedding compliance into your IP strategy, we help mitigate the risk of unintentional violations, protect your innovations, and maintain your organization’s reputation across markets.

Cyber Insurance Audit
In today’s digital age, protecting your intellectual property from cyber threats is crucial. Our Cyber Insurance Audit assesses whether your organization’s current cyber insurance coverage adequately protects your IP assets. We review your policies to ensure that they cover potential risks to intellectual property such as theft, data breaches, and cyberattacks. By conducting a thorough audit, we identify gaps in coverage and provide recommendations to ensure that your IP is fully protected in case of a cyber incident. This audit helps ensure that your organization is not exposed to financial losses or legal challenges related to the theft or loss of intellectual property.

Enterprise Security Strategy Consulting
A comprehensive Enterprise Security Strategy is essential to protecting your intellectual property from internal and external threats. Our consulting services focus on integrating IP protection into your organization’s overall security strategy. We assess your current security measures, including data protection, access controls, encryption, and threat monitoring, and ensure that your IP is properly safeguarded at every stage of its lifecycle. We also work with your leadership team to align IP security goals with broader business objectives, ensuring that your strategy mitigates risks and protects your intellectual property from cyberattacks, employee misuse, and theft.
Supply Chain Security Review
Intellectual property can be vulnerable in the supply chain, where third-party vendors and partners may inadvertently or intentionally expose valuable assets. Our Supply Chain Security Review focuses on identifying potential risks related to the handling and protection of IP within your supply chain. We assess your suppliers’ and partners’ security practices to ensure that your IP is protected throughout its lifecycle—from development to distribution. By conducting thorough due diligence and establishing strong security protocols with third parties, we help reduce the risk of IP theft, counterfeiting, or leakage during manufacturing, transportation, or collaboration.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
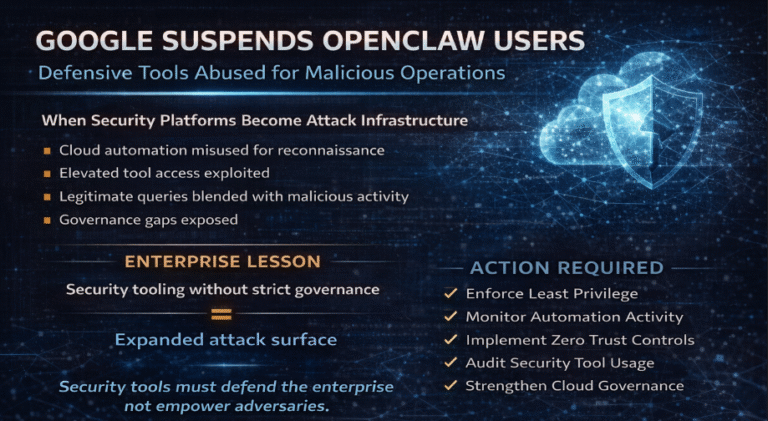
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…