Center of Excellence Security - Cyber Insurance Audit
Strengthen Your Cyber Risk Management with Precision!
Optimize your cyber insurance coverage, identify gaps, and secure your assets with our expert audit services.
Cyber Insurance Audit at COE Security

At COE Security, we understand the critical role that cyber insurance plays in protecting your business against the financial impacts of cyberattacks. Our Cyber Insurance Audit service helps organizations assess their cybersecurity posture and ensure they meet the necessary requirements to obtain or renew their cyber insurance policies.
In today’s increasingly regulated environment, insurers are demanding higher standards of security from businesses before offering coverage. We perform a thorough audit of your current cybersecurity measures to identify gaps in your defenses and determine whether they align with the specific requirements set by your insurer. By aligning your organization with best practices and industry standards, we help improve your chances of securing comprehensive coverage at competitive rates.
Our team leverages industry-leading frameworks such as NIST, ISO 27001, and CIS to assess your security controls and risk management practices. The results of our audit will provide a clear roadmap for remediation, making it easier for your organization to meet insurer requirements and strengthen its overall security posture.
Our Approach
Assess Current Cyber Insurance Coverage: Review existing cyber insurance policies to determine coverage limits, exclusions, and terms to ensure they align with your organization’s risk profile.
Identify Gaps in Coverage: Compare the existing insurance policy against potential cyber threats and risks, identifying areas where coverage may be insufficient or lacking.
Evaluate Risk Management Practices: Assess the effectiveness of current cybersecurity measures, including data protection, incident response, and risk management, to determine eligibility for premium discounts.
Review Compliance with Industry Standards: Ensure that the organization’s cybersecurity practices meet or exceed the standards required by the insurance provider for coverage, such as NIST, ISO, or GDPR.
Analyze Incident History and Claims Data: Review past incidents and claims to understand patterns, vulnerabilities, and lessons learned to ensure better risk mitigation and future claims management.
Evaluate Third-Party Risk Exposure: Examine how third-party vendors and partners impact your cyber risk and whether third-party risks are adequately covered by the current policy.
Assess Coverage for Emerging Threats: Ensure that the policy covers emerging cyber threats, such as ransomware, supply chain attacks, and advanced persistent threats (APTs), which may not have been considered in older policies.
Review Policy Terms and Conditions: Analyze the terms and conditions of the cyber insurance policy to ensure there are no ambiguities that could affect claims eligibility or the payout process.
Assess Claims Process and Response Times: Review the insurer’s claims handling process, response times, and the overall efficiency of resolving cyber incidents to ensure that support will be timely during a breach.
Recommend Adjustments and Optimizations: Provide recommendations for updating or optimizing cyber insurance coverage to fill any identified gaps and better align with the organization’s evolving risk landscape.
Risk Assessment & Evaluation
Coverage Gap Identification
Compliance Verification
Claims Process Optimization
Cyber Insurance Audit Process
Our proven cyber insurance audit methodology provides thorough assessments and detailed recommendations, ensuring your coverage aligns with your organization’s risk profile and compliance requirements.
Assess
Analyze
Identify Gaps
Report & Recommend
Optimize
Why Choose COE Security’s Cyber Insurance Audit?
Comprehensive Coverage Review: We provide a thorough evaluation of your current cyber insurance policy to ensure it provides adequate protection for your business.
Identification of Coverage Gaps: We identify any gaps in your cyber insurance coverage, ensuring that you’re fully protected against potential risks.
Alignment with Industry Standards: Our audits ensure that your cybersecurity measures align with industry best practices and meet the insurer’s requirements for premium optimization.
Risk Management Optimization: We assess your current cybersecurity measures and provide recommendations to improve them, which can result in cost savings on your premiums.
Tailored Coverage Recommendations: Our consultants help you secure the best cyber insurance coverage by recommending adjustments that are specific to your organization’s needs.
Support for Emerging Threats: We ensure your policy adequately addresses emerging risks like ransomware and advanced cyber-attacks that could impact your business.
Third-Party Risk Consideration: We evaluate third-party relationships to ensure that vendor and partner-related risks are covered under your cyber insurance policy.
Clear Understanding of Policy Terms: We help you understand the fine print, ensuring there are no ambiguities that could affect your ability to make a claim.
Streamlined Claims Process Review: We review the insurer’s claims handling process to ensure it is efficient and will provide support during a cyber incident.
Continuous Risk Coverage Adjustments: We offer ongoing support to help you adapt your coverage as your risk profile changes, ensuring your business remains protected.
Five areas of Cyber Insurance Audit

Compliance as a Service
Ensuring regulatory compliance is crucial to avoiding penalties and maintaining customer trust. Our Compliance as a Service training helps your team stay up-to-date with complex and ever-changing regulations such as GDPR, HIPAA, PCI DSS, and more. We provide comprehensive support in assessing your compliance posture, identifying gaps, and implementing measures to meet industry standards. Our expert consultants guide you through the compliance process, integrating security best practices and risk management frameworks to ensure that your security program is both effective and compliant. This service minimizes your risk exposure while reinforcing your overall security strategy.
Supply Chain Security Review
A Supply Chain Security Review is critical in the Cyber Insurance Audit process. Supply chain vulnerabilities are often a significant risk that many businesses overlook, but cyberattacks targeting suppliers, contractors, or service providers can lead to severe financial losses. Our experts evaluate the security posture of your third-party vendors, assess risks related to third-party access to your systems, and ensure that their security practices align with your organization’s standards. A thorough review ensures that your suppliers maintain the required level of security, which is increasingly demanded by insurers. By addressing third-party risks, we help you ensure that your insurance coverage extends to potential breaches originating from your supply chain.

Legal Risk Review
Expanding your business into new regions can expose your organization to unique legal risks, especially concerning data privacy laws and cybersecurity regulations. Our Legal Risk Review in New Territories service evaluates the legal and regulatory requirements in the jurisdictions you’re entering. We help you navigate different laws around data protection, cybersecurity, and compliance, ensuring that your cyber insurance policy is tailored to meet local requirements. By proactively addressing these legal risks, we help you avoid future compliance challenges, protecting your organization from the financial and operational impact of legal issues, especially in unfamiliar regions or countries with stringent regulations.

Security Program Development
A robust Security Program Development is a cornerstone of a solid Cyber Insurance Audit. Insurers typically require evidence of comprehensive security measures to minimize the risk of a cyber incident. We help you develop and implement a tailored security program that covers all aspects of your cybersecurity strategy, including risk assessments, threat detection, security controls, and incident response. A strong security program not only helps mitigate risk but also demonstrates to insurers that your organization is taking proactive steps to protect its assets and data. This can lead to better policy terms, lower premiums, and, in some cases, enhanced coverage based on your organization’s cybersecurity posture.

Enterprise Security Strategy Consulting
Developing a strong enterprise security strategy is essential to protecting your organization’s assets and maintaining operational resilience. Our Enterprise Security Strategy Consulting service helps you design and implement a security roadmap aligned with your business objectives. We assess your current security posture, identify vulnerabilities, and develop a tailored strategy incorporating best practices, threat intelligence, and compliance requirements. Our expert consultants work closely with your team to integrate governance, risk management, and security architecture into a cohesive framework. This proactive approach strengthens your defenses, improves incident response readiness, and ensures long-term security maturity across the enterprise.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
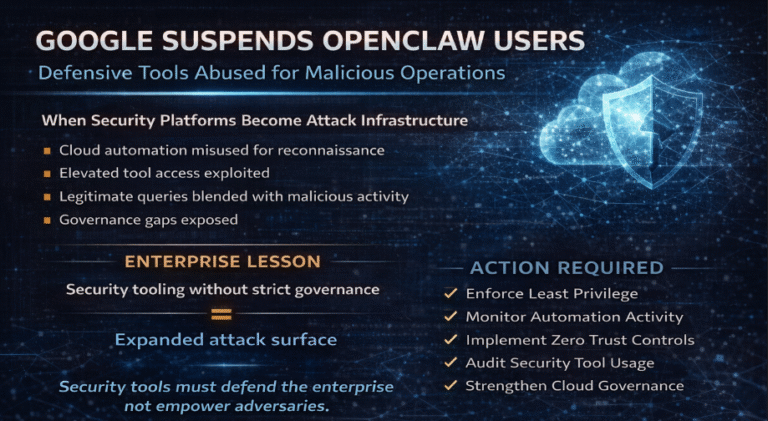
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…