Center of Excellence Security - Blockchain Monitoring & Incident Response
Stay Ahead of Blockchain Threats - Always!
With continuous monitoring and rapid response, we protect your network against real-time risks, exploits, and chain disruptions.
Blockchain Monitoring & IR at COE Security

COE Security’s Ongoing Security Monitoring & Incident Response for Blockchain provides relentless, real-time surveillance of blockchain environments, smart contract behavior, and API activity. Our service blends custom SIEM rules, blockchain analytics, and active threat hunting to detect anomalies like token drain, flash-loan manipulation, and data exfiltration. Tailored alert workflows and incident playbooks enable security teams to act fast, whether via scheduled monitoring or ad-hoc after significant updates. You receive high-priority alerts, forensic reports, and remediation plans to contain threats, recover assets, and resume operations swiftly. This continuous visibility across on-chain events, off-chain infrastructure, and backend systems maintains resilience against evolving adversarial tactics in DeFi, enterprise chains, and institutional deployments.
Our Approach
-
Define assets and event types to monitor, including smart contracts, node behavior, on-chain transactions, wallet activity, and protocol configuration changes.
-
Deploy monitoring agents and sensors across the environment to collect telemetry, logs, and behavior metrics in real time.
-
Establish anomaly detection rules to flag suspicious activity like flash-loan spikes, unauthorized governance actions, or bridge exploits.
-
Integrate alerts into your SOC via SIEM, SOAR, or incident management tools for fast triage and response.
-
Develop and document incident response workflows, including alert classification, containment, forensic preservation, and escalation procedures.
Enable real-time containment measures, such as halting protocol execution, blacklisting addresses, or disabling compromised validators.
Ensure immutable forensic logging, with blockchain-anchored or tamper-resistant audit trails for legal and compliance use.
Conduct incident simulation exercises, helping stakeholders rehearse their response to realistic threats and improve playbook readiness.
Perform post-incident analysis to extract lessons, improve detection logic, and reduce the time to containment in future scenarios.
Continuously refine monitoring posture, adapting to new threat trends, platform upgrades, and operational changes.
Threat Surface Mapping
Behavior-Based Detection
Incident Triage & Forensics
Response & Containment
Blockchain Monitoring & Incident Response Process
Our established blockchain monitoring & incident response methodology delivers comprehensive testing and actionable recommendations.
Baseline Behavior Modeling
Threat Intelligence Integration
Real-Time Monitoring
Incident Response Playbooks
Continuous Improvement
Why Choose COE Security’s Blockchain Monitoring & IR?
24×7 Blockchain Threat Surveillance – Detect abnormal activity on-chain and across infrastructure.
DeFi Protocol Monitoring – Spot flash loan attacks, oracle manipulations, and other rapid exploit attempts.
SIEM & SOAR Integration – Correlate on-chain events with traditional logs for unified response.
Real-Time Alerting – Receive instant alerts for critical activities, contract changes, and suspicious wallet behavior.
Forensic-Ready Architecture – Retain logs and metadata optimized for incident investigation.
Smart Contract Behavior Anomaly Detection – AI-based detection of out-of-spec execution.
Incident Playbooks for Blockchain – Custom-tailored response guides for common attack scenarios.
Crisis Communications Support – Guidance on investor and public disclosure during an incident.
Post-Incident Remediation – Assistance in patching vulnerabilities and securing compromised assets.
Red Team Simulation & Drills – Test organizational readiness with blockchain-specific attack simulations.
Five Areas Section of Blockchain Monitoring & IR

Penetration Testing as a Service
Our Penetration Testing as a Service (PTaaS) provides continuous, on-demand security testing for thick client applications. Unlike web or mobile applications, thick client applications are often installed locally on users’ devices and have unique security concerns. With PTaaS, we simulate real-world attacks on your thick client apps, focusing on vulnerabilities such as insecure data storage, improper session handling, code injection, and client-side security flaws. Through regular and comprehensive testing cycles, we uncover hidden vulnerabilities that could be exploited by attackers, ensuring that your application is secure, resilient, and prepared for any potential threats.
Application Security Consulting
Our Application Security Consulting services are designed to integrate security into every phase of your thick client application development lifecycle. We work with your development team to identify potential security risks early and provide guidance on implementing best practices for secure coding, architecture, and testing. From securing data storage to hardening communication channels, our experts help you build a strong security foundation for your thick client applications. Additionally, we assist in conducting threat modeling, static code analysis, and risk assessments to ensure that your thick client apps are secure against both internal and external threats.
We also address risks unique to thick clients, such as local data exposure and reverse engineering. Our approach helps reduce rework, accelerates secure development, and ensures long-term application integrity.

Software Compliance Testing
Compliance with industry standards and regulations is essential, even for thick client applications. Our Software Compliance Testing service ensures that your thick client applications meet the required regulatory frameworks, including GDPR, HIPAA, PCI-DSS, and others. We conduct detailed assessments to ensure that your software adheres to security, data privacy, and accessibility standards. By performing thorough compliance testing, we help you identify any gaps or non-compliance areas that could lead to penalties, data breaches, or reputational damage. Our testing provides you with the assurance that your thick client application meets legal and regulatory requirements, minimizing legal and operational risks.

Secure Software Development Consulting
Secure development practices are crucial when building thick client applications to ensure that security vulnerabilities are mitigated during the development phase. Our Secure Software Development Consulting services guide your team in adopting secure coding techniques and integrating security into the software development lifecycle (SDLC). We provide hands-on support in threat modeling, secure architecture design, and vulnerability management, ensuring that your thick client applications are built with security in mind from the very beginning. By applying secure development practices, we reduce the risk of introducing security flaws, ensuring that your applications are resistant to exploits, such as buffer overflows, insecure deserialization, and privilege escalation.

Application Security Posture Management
Application Security Posture Management is a continuous, proactive approach to managing and improving the security of your thick client applications. We help you monitor your application’s security posture over time, ensuring that new vulnerabilities are quickly identified and mitigated. This includes regular vulnerability assessments, patch management, and threat intelligence integration to stay ahead of emerging threats. Our team provides ongoing support to address security gaps, track the effectiveness of security controls, and ensure that your application’s security posture is always up to date. By maintaining a strong security posture, we help you protect your thick client applications from evolving cyber threats.
Advanced Offensive Security Solutions
COE Security empowers your organization with on-demand expertise to uncover vulnerabilities, remediate risks, and strengthen your security posture. Our scalable approach enhances agility, enabling you to address current challenges and adapt to future demands without expanding your workforce.
Why Partner With COE Security?
Your trusted ally in uncovering risks, strengthening defenses, and driving innovation securely.
Expert Team
Certified cybersecurity professionals you can trust.
Standards-Based Approach
Testing aligned with OWASP, SANS, and NIST.
Actionable Insights
Clear reports with practical remediation steps.
Our Products Expertise















Information Security Blog
Essential e-Signature Solutions for Cybersecurity
As digital transformation accelerates, electronic signatures have become a core part of…
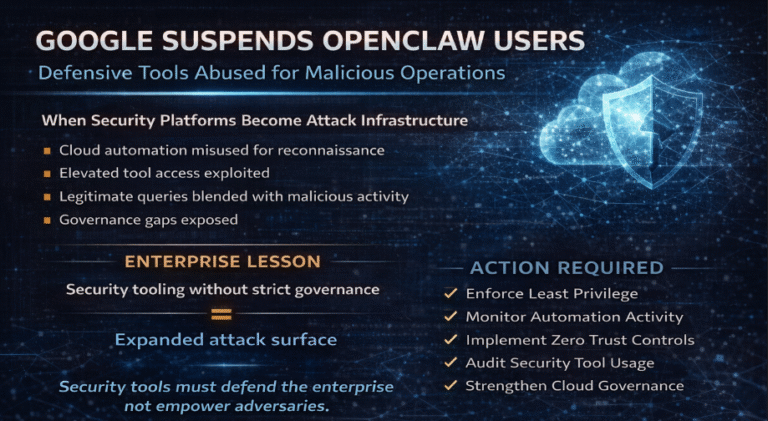
Google Suspends OpenClaw Accounts Amid Malware Abuse – What Security Teams Must Know
In a proactive security move, Google has suspended a number of OpenClaw…
Critical VoIP Security Alert: Grandstream GXP1600 Phones Exposed to Remote Code Execution Risk
A newly released proof of concept exploit targeting Grandstream GXP1600 series VoIP…