Grafana Ghost: Silent Threat

Some vulnerabilities don’t shout, they whisper. They linger quietly, waiting for a misstep, a click, an unpatched system. CVE-2025–4123, ominously dubbed The Grafana Ghost, is one such vulnerability. Discovered by security researcher Alvaro Balada, this client-side open redirect flaw in Grafana, an open-source observability platform, presents a surprisingly stealthy pathway for attackers. It was patched by […]
Defender Flaw: AD at Risk

In the ever-evolving world of cybersecurity, it’s not always the loudest exploits that do the most damage. Sometimes, it’s the silent ones hidden in routine tools that breach the deepest. A newly disclosed vulnerability (CVE-2025–26685) in Microsoft Defender for Identity (MDI) has drawn just such a line in the sand. Though rated a modest 6.5 […]
Human Firewall: 2025 Guide
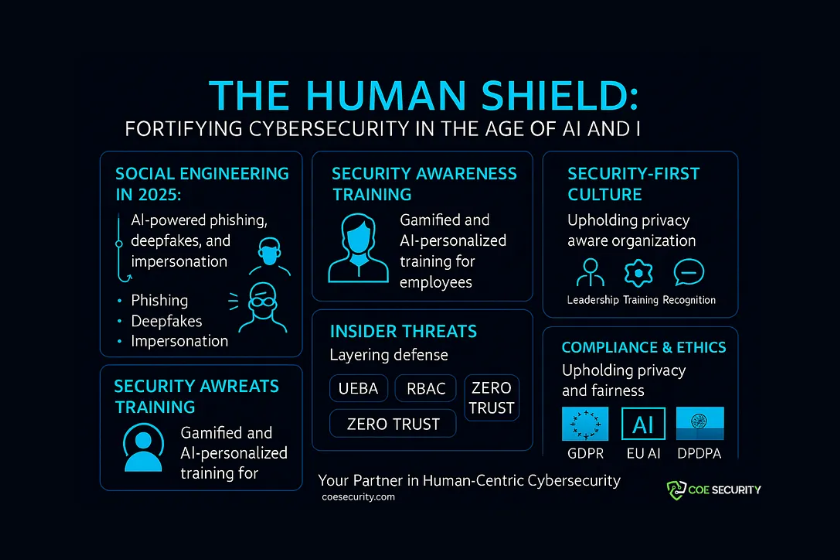
The Human Core of Cybersecurity in 2025 The digital landscape of 2025 is a battleground where technology and human behavior collide.1 With 27 billion connected devices, global cybercrime costs projected to exceed $10 trillion annually, and 95% of breaches tied to human error, the human element has emerged as both the greatest vulnerability and the […]
SFireTruck & HelloTDS Threat
In the dim shadows of trusted websites, an unfamiliar script is silently weaving chaos. This is not the usual brute-force or phishing campaign; it’s far more discreet, calculated, and steeped in obfuscation. Recent reports by Palo Alto Networks’ Unit 42 have revealed an expansive malicious campaign exploiting JavaScript injections. The obfuscation method, known as JSFuck, repurposes […]
Discord Invites: Hacker Trap

Some doors, even after they close, can still be opened especially in the digital realm. In a recently uncovered cyber campaign, attackers are exploiting expired or deleted Discord invite links to lure unsuspecting users into malware traps. What appears to be an expired key becomes a gateway to remote access trojans, info-stealers, and persistent infections, […]
TeamFiltration: Cloud Threat

The line between ethical penetration testing and real-world exploitation has never been thinner. TeamFiltration, a legitimate open-source framework designed for red teaming, is now emerging as a preferred weapon in the arsenal of malicious actors targeting Microsoft Entra ID (formerly Azure Active Directory). A new wave of attacks, identified as UNK_SneakyStrike by researchers at Proofpoint, is exploiting […]
VexTrio: Silent Traffic Web

In the ever-evolving terrain of cyber threats, not all danger wears the mask of ransomware or brute-force attacks. Some threats hide in plain sight behind a single click, a banner ad, or a seemingly harmless website redirect. One such growing menace is the VexTrio Viper Traffic Distribution Service (TDS), a silent but sprawling digital syndicate […]
EchoLeak: AI Hijack Threat

In the era of AI-driven productivity, convenience often overshadows caution. The recent exposure of EchoLeak, a zero-click exploit targeting Microsoft 365 Copilot, forces us to confront a growing and silent threat our AI assistants might be too obedient for their own good. Revealed by AI security firm Aim Security, EchoLeak exploited a vulnerability (CVE-2025–32711) that allowed […]
Shadows of Ransom Tactics

In the ever-evolving terrain of cyber threats, not all danger wears the mask of ransomware or brute-force attacks. Some threats hide in plain sight behind a single click, a banner ad, or a seemingly harmless website redirect. One such growing menace is the VexTrio Viper Traffic Distribution Service (TDS), a silent but sprawling digital syndicate […]
Safeguarding 27 Billion Devices in 2025

Introduction: The IoT Revolution and Its Security Imperative The Internet of Things has profoundly transformed modern society, creating a vast network of interconnected devices that drive innovation across every industry. From smart thermostats optimizing home energy consumption to sophisticated sensors enhancing factory floors, IoT’s influence is extensive and groundbreaking.2 In 2024, there were 18.8 billion […]
