Penetration testing is evolving
Penetration testing is evolving. As applications grow more complex, traditional approaches built around broad scanning and manual reconnaissance are increasingly inefficient. Modern environments span APIs, cloud-native architectures, client-side logic, and third-party integrations. While tooling has advanced, much of a pentester’s time is still spent identifying where to look rather than validating what actually matters. This […]
What Enterprises Must Address Now

As organizations accelerate the adoption of agentic AI systems, security leaders must prepare for a new class of risks. Unlike traditional AI models that simply respond to prompts, agentic AI systems can plan, make decisions, interact with tools, and execute tasks autonomously. While this unlocks powerful automation capabilities, it also significantly expands the attack surface. […]
Windows 11 KB5077181 Update Causes Restart Loop on Select Devices
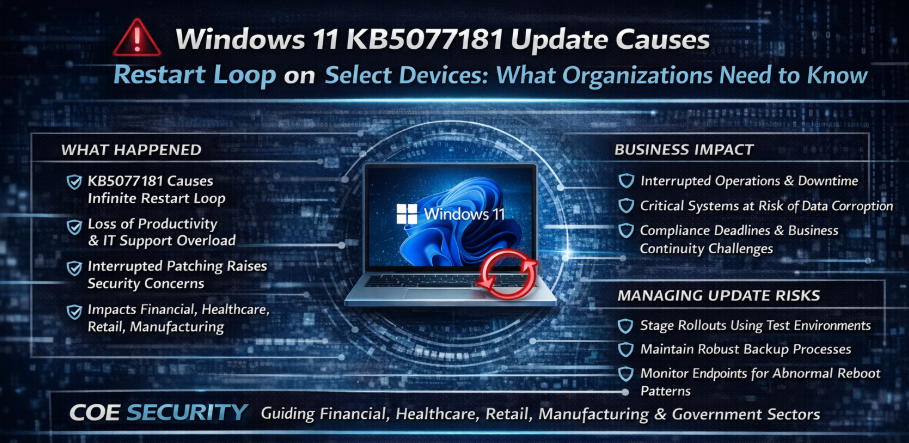
A recent update for Windows 11, identified as KB5077181, has reportedly triggered an infinite restart loop on certain devices. While regular updates are critical for patching vulnerabilities and improving performance, this incident highlights the operational risks that can arise when updates conflict with specific hardware configurations or software environments. For enterprises managing thousands of endpoints, […]
Threat Actors Are Targeting Shoppers and Business

In 2026, cybercriminals are taking e-commerce fraud to a new level with highly convincing fake shops designed to lure shoppers and steal data. A recent threat report reveals that attackers are exploiting the popularity of major events and consumer demand to launch networks of fraudulent online stores that impersonate well-known brands and steal payment and […]
DNS Hijacking Emerges as a Scalable Malware Distribution Tactic

Cyber threats continue to evolve, and the latest ClickFix campaign highlights a dangerous shift toward infrastructure level manipulation. In this wave of attacks, threat actors are combining DNS hijacking with advanced social engineering to redirect users to malicious sites that deliver malware disguised as routine fixes or security updates. This tactic is both technically sophisticated […]
AI Platforms and Search Ads Exploited to Deliver Malware

Cybercriminal tactics are evolving again. A recent campaign uncovered how attackers abused AI generated content platforms such as Anthropic’s Claude Artifacts and malicious advertising through Google Ads to distribute malware targeting macOS users. This marks a significant shift in strategy. Rather than exploiting traditional software vulnerabilities, threat actors are manipulating trusted ecosystems including AI tools […]
serious and unsettling security development

In today’s interconnected enterprise environments, firewalls represent the first and last line of defense. They sit at the network perimeter, enforce access controls, inspect traffic, and protect critical internal systems. Yet, in the last 24 hours, a serious and unsettling security development has emerged: Fortinet FortiGate firewalls are being actively compromised through a FortiCloud SSO […]
The Convergence of Hardware Exploits, Artificial Intelligence Driven Threats, and Modern Ransomware

The global cybersecurity landscape is undergoing a structural shift. Attackers are no longer relying solely on traditional phishing emails or opportunistic malware campaigns. Instead, we are witnessing the convergence of hardware manipulation techniques, artificial intelligence assisted attack operations, and increasingly adaptive ransomware ecosystems. For enterprises across regulated and critical industries, this evolution represents more than […]
The Convergence of Hardware Exploits, Artificial Intelligence Driven Threats, and Modern Ransomware The global cybersecurity landscape is undergoing a structural shift. Attackers are no longer relying solely on traditional phishing emails or opportunistic malware campaigns. Instead, we are witnessing the convergence of hardware manipulation techniques, artificial intelligence assisted attack operations, and increasingly adaptive ransomware ecosystems. […]
Active Exploitation of SolarWinds Web Help Desk

Security teams are confirming active exploitation of a critical vulnerability in SolarWinds Web Help Desk, allowing attackers to achieve remote code execution (RCE) on systems that often operate with elevated privileges. This is not just another software flaw. It represents a broader and more dangerous shift in attacker strategy: IT management and help desk platforms […]
